- Course
Configuring Security Headers in ASP.NET 4 and ASP.NET Core 3 Applications
After watching this course you'll have the knowledge and skills to mitigate common browser attacks by setting HTTP headers. The code samples are in ASP.NET Core and ASP.NET for .NET Framework.
- Course
Configuring Security Headers in ASP.NET 4 and ASP.NET Core 3 Applications
After watching this course you'll have the knowledge and skills to mitigate common browser attacks by setting HTTP headers. The code samples are in ASP.NET Core and ASP.NET for .NET Framework.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
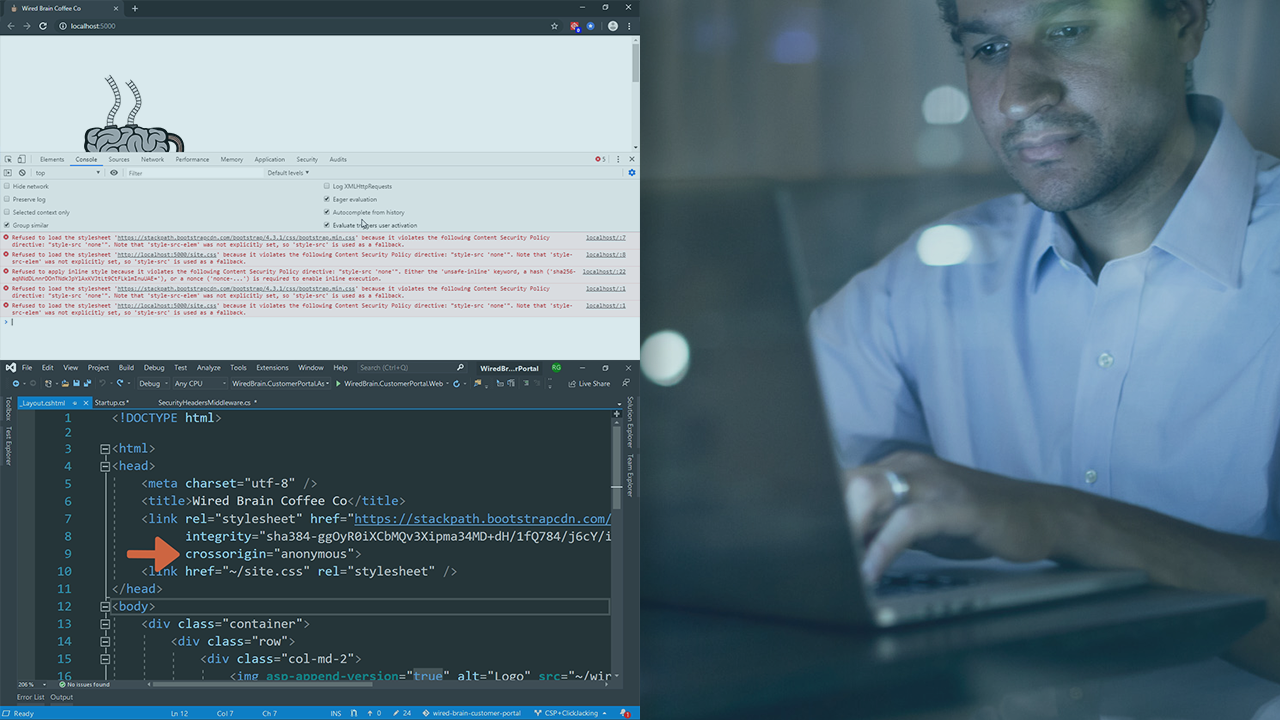
You’ve heard about attacks like Cross Site Scripting (CSS) and click-jacking. This course, Configuring Security Headers in ASP.NET and ASP.NET Core Applications, will give you the skills needed to mitigate these kinds of attacks by turning on browser features in your ASP.NET(Core) application like Content Security Policy (CSP), Referrer Policy and Feature Policy. By the end of this course you'll not only know how to make these configurations, you'll understand how these attacks work.
Configuring Security Headers in ASP.NET 4 and ASP.NET Core 3 Applications
-
Version Check | 15s
-
Module Overview | 42s
-
The Browser Is Unsafe: How HTTP Headers Can Help | 3m 46s
-
Adding HTTP Headers to the Response with Filters | 2m 41s
-
Using Middleware to Add HTTP Headers | 2m 8s
-
Emitting HTTP Headers Using the Web.Config and NWebSec | 1m 14s
-
Determining Which Security Headers Are Needed | 1m 15s
-
Summary | 52s

