- Course
Automating Cisco Endpoint Security Solutions Using APIs
Inserting security appliances into your enterprise network is necessary but not sufficient. This course will teach you how to programmatically manage Cisco AMP, ThreatGrid, and Umbrella to provide next-generation protection for endpoints.
- Course
Automating Cisco Endpoint Security Solutions Using APIs
Inserting security appliances into your enterprise network is necessary but not sufficient. This course will teach you how to programmatically manage Cisco AMP, ThreatGrid, and Umbrella to provide next-generation protection for endpoints.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
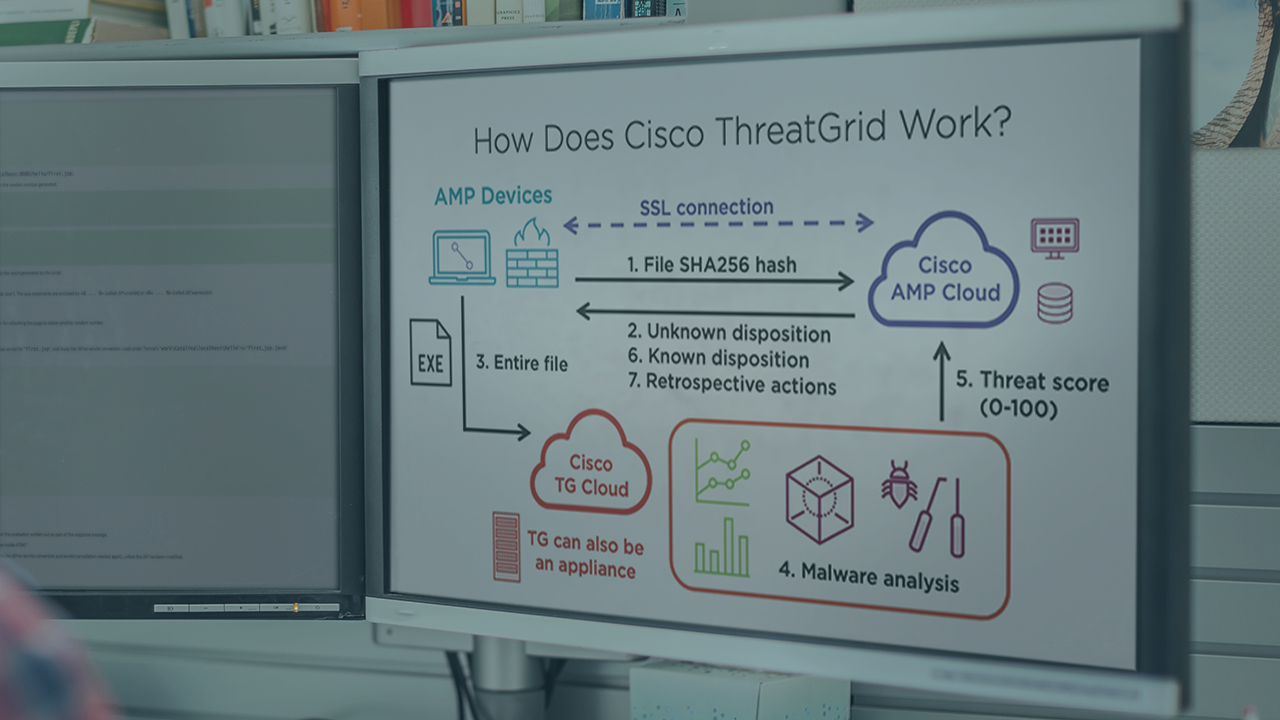
Endpoint security is often overlooked or deferred in the context of enterprise security due to challenges with scalable management. Leveraging automation can greatly simplify endpoint security operations. In this course, Automating Cisco Endpoint Security Solutions Using APIs, you'll explore Cisco's flagship anti-malware product, Advanced Malware Protection (AMP) for endpoints, and interact with it using a robust REST API. Next, you'll discover how to improve the effectiveness of AMP by tying it into ThreatGrid, a detonation chamber for suspected malware, again using the REST API. Finally, you'll learn how to protect roaming users from Internet attacks using Cisco Umbrella, a cloud-hosted, DNS-based security service. Specifically, we’ll focus on the Umbrella Reporting, Enforcement, and Investigate APIs. When you're finished with this course, you'll have the skills and knowledge of security endpoint management to operate and maintain modern solutions at scale using automation.
Automating Cisco Endpoint Security Solutions Using APIs
-
Course Introduction, Prerequisites, and Business Scenario | 2m 28s
-
Update: Cisco Security Product Renaming | 1m 28s
-
How Does Cisco AMP Work? | 4m 46s
-
Demo: Downloading Malware and Installing AMP on Windows | 4m 4s
-
Demo: Getting Started with the AMP API | 4m 29s
-
Demo: Building a Hierarchical SDK Framework | 8m 25s
-
Demo: Scanning for Malware Using AMP | 6m 38s
-
Demo: Changing Computer Group Assignments | 4m 17s
-
Demo: Blocking Custom Applications | 6m 13s
-
Module Summary and Homework Challenge | 55s

