- Course
Securing Connected Devices with AWS IoT Device Defender
As the number of AWS IoT devices in your environment grows, it is important to properly monitor and secure them. This course will introduce the AWS Device Defender tool to help you secure your IoT environment.
- Course
Securing Connected Devices with AWS IoT Device Defender
As the number of AWS IoT devices in your environment grows, it is important to properly monitor and secure them. This course will introduce the AWS Device Defender tool to help you secure your IoT environment.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Cloud
- Security
What you'll learn
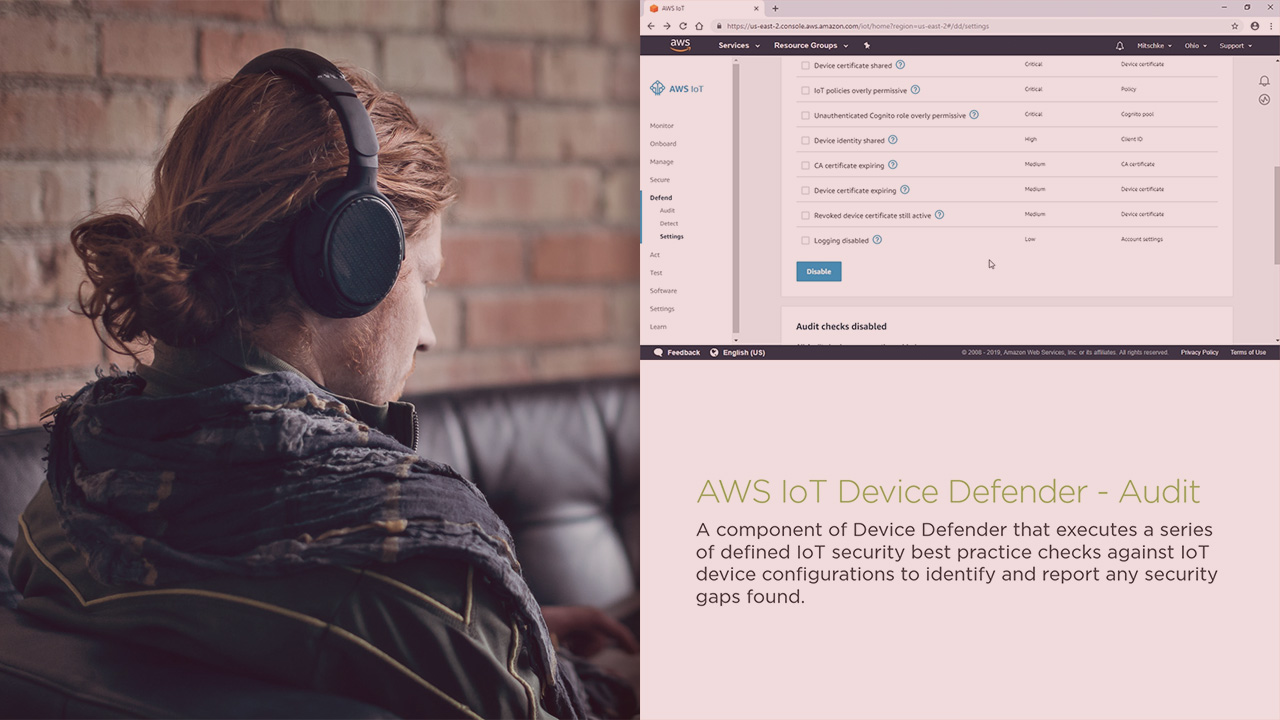
Being aware of issues within an environment with many devices can be a challenging task. Internet of Things (IoT) can be especially difficult due to the scale opportunities that exist. AWS has provided a tool called Device Defender to help you stay on top of potential security issues that may exist in your IoT environments. In this course, Securing Connected Devices with AWS IoT Device Defender, you will explore configuring Device Defender to monitor and secure your IoT environment. First, you will learn how to configure and use Device Defender Audit to set up audits to monitor your IoT environments using industry best practice checks. Next, you will discover how to configure and use Device Defender Detect to monitor IoT device metrics to alarm on anomalies. Finally, you will learn how to configure Mitigation Actions to automatically react to a variety of issues that can occur in your environment. When you’re finished with this course, you will have the skills and knowledge to configure Audit, Detect, and Mitigation Actions within AWS IoT Device Defender to monitor and secure your IoT environment.

