- Course
Command and Control with Covenant
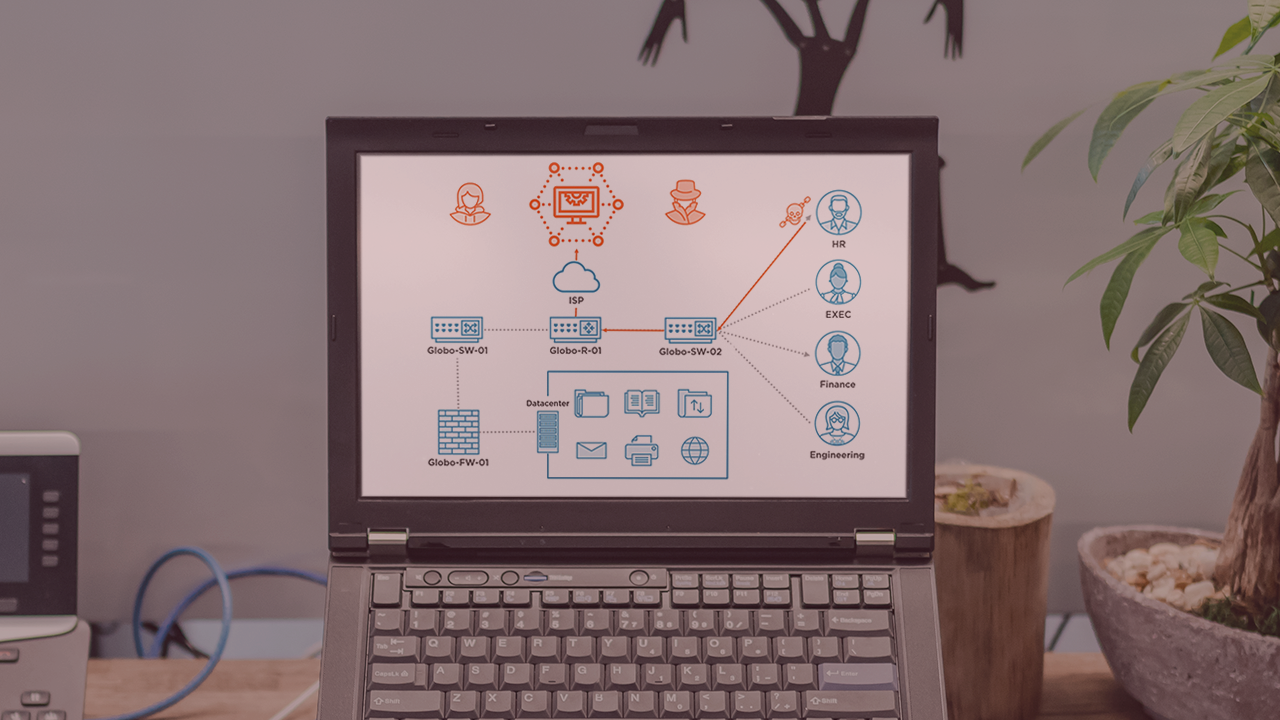
Covenant C2 command and control uses just-in-time, in-memory, .NET compilation, and dynamic profiles to fool defensive detections. Skill up your red team techniques by leveraging the next generation of adversary command and control capabilities.
- Course
Command and Control with Covenant
Covenant C2 command and control uses just-in-time, in-memory, .NET compilation, and dynamic profiles to fool defensive detections. Skill up your red team techniques by leveraging the next generation of adversary command and control capabilities.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Testing systems against advanced adversary techniques is required not just for red team operations but for targeted testing of defensive and detective measures on a network. Growing the skills to emulate the steadily advancing adversary capabilities within your team is a moving target that is complicated by the multitude of attack techniques available. In this course, Command, and Control with Covenant, you will gain the ability to leverage the advanced .NET, in-memory compilation techniques used by the open-source Covenant project to emulate adversary communication within an environment. First, you will learn to install the command and control infrastructure used to control compromised systems. Next, you will explore how to create and install implants called grunts to connect back to the adversary server. Finally, you will explore how to run tasks, gather information, and spread laterally within the Covenant C2 framework. When you are finished with this course, you will have the skills and knowledge of the Covenant command and control framework needed to emulate post-exploitation techniques aligned with Mitre ATT&CK.

