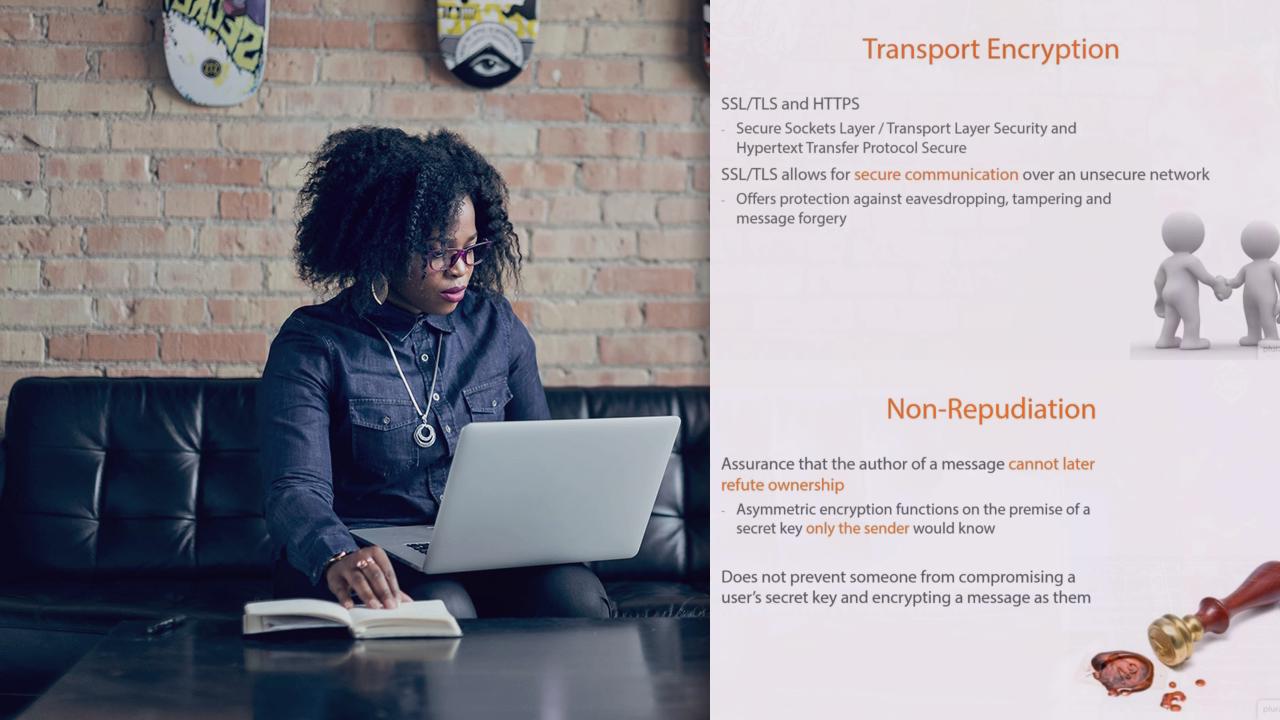
- Course
CompTIA Security+ (SY0-401) Cryptography
CompTIA Security+ (2014 Objectives): Domain 6 - Cryptography
- Course
CompTIA Security+ (SY0-401) Cryptography
CompTIA Security+ (2014 Objectives): Domain 6 - Cryptography
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
CompTIA Security+ (2014 Objectives) prepares networking and IT professionals with the required knowledge and skills to understand the concepts and technologies involved with encryption, cryptography, PKI, and the associated benefits and risks.

