- Course
Configuring and Managing Kubernetes Security
This course will teach you the fundamentals needed to configure and manage security in Kubernetes clusters.
- Course
Configuring and Managing Kubernetes Security
This course will teach you the fundamentals needed to configure and manage security in Kubernetes clusters.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
In this course, Configuring and Managing Kubernetes Security, you’ll learn the foundations needed for securing access to your Kubernetes Cluster. First, you’ll explore Kubernetes security fundamentals, learning how authentication and authorization work to control access to the Kubernetes API. Then, you’ll learn how certificates are used in Kubernetes and how to create and manage certificates in your cluster. Next, you’ll learn how to create and manage kubeconfig files for accessing clusters and then configure cluster access for a new user. Finally, you’ll learn how to control access to the Kubernetes API with role based access controls. When you’re finished with this course you will have the skills needed to operate and manage security in Kubernetes clusters. This course can also help you prepare for your Certified Kubernetes Administrator (CKA) certification.
Configuring and Managing Kubernetes Security
-
Introduction, Course, and Module Overview | 1m 55s
-
Securing the API Server and Authentication Plugins | 5m 58s
-
Users in Kubernetes | 2m 45s
-
Service Accounts and Service Account Credentials | 3m 46s
-
Creating a Service Account and Defining a ServiceAccount in a Pod Spec | 3m 6s
-
Demo: Investigating Certificate Based Authentication | 4m 46s
-
Demo: Working with Service Accounts | 3m 47s
-
Demo: Accessing the API Server Inside a Pod | 4m 51s
-
Demo: Testing API Access with kubectl can-i with Impersonation | 1m 58s
-
Authorization Plugins | 1m 39s
-
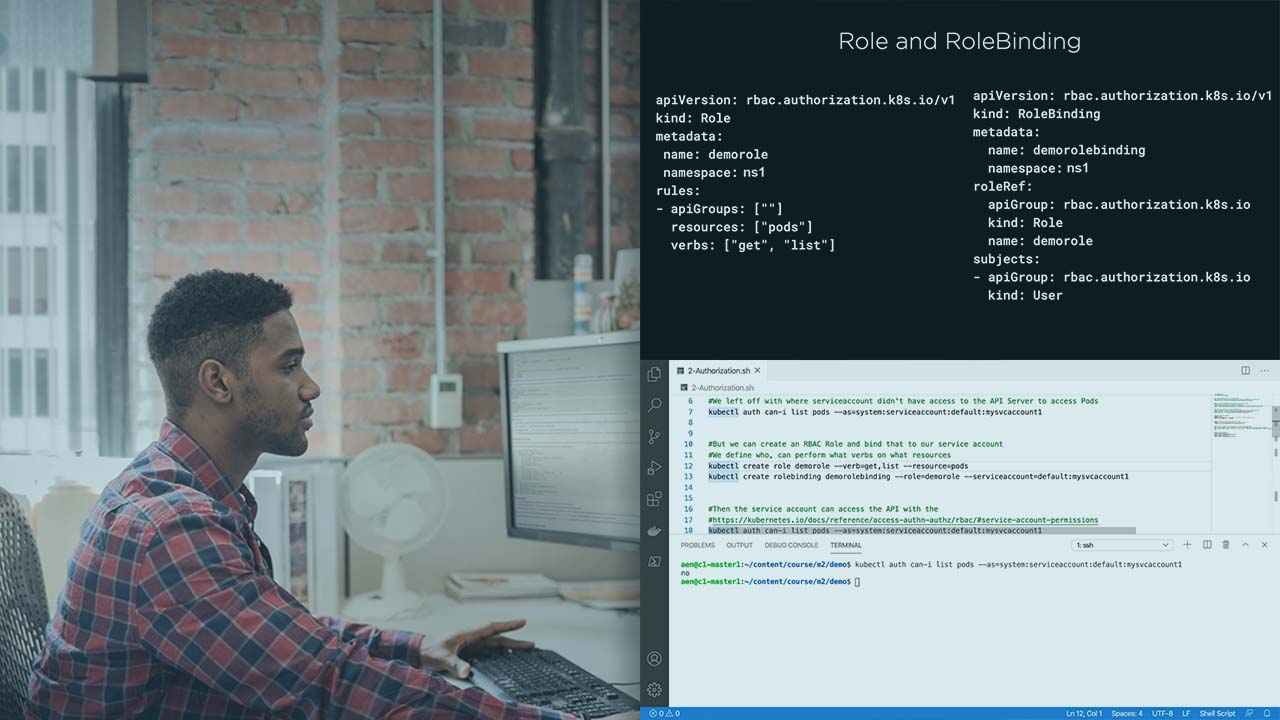
Demo: Managing Authorization for Service Accounts | 4m 19s
-
Module Review and What's Next! | 39s

