- Course
Container Infrastructure Analysis with kube-hunter
Want to learn how to analyze (and prevent) security weaknesses in Kubernetes? If so, you're in the right place! In this course, you will learn Container Infrastructure Analysis with kube-hunter.
- Course
Container Infrastructure Analysis with kube-hunter
Want to learn how to analyze (and prevent) security weaknesses in Kubernetes? If so, you're in the right place! In this course, you will learn Container Infrastructure Analysis with kube-hunter.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
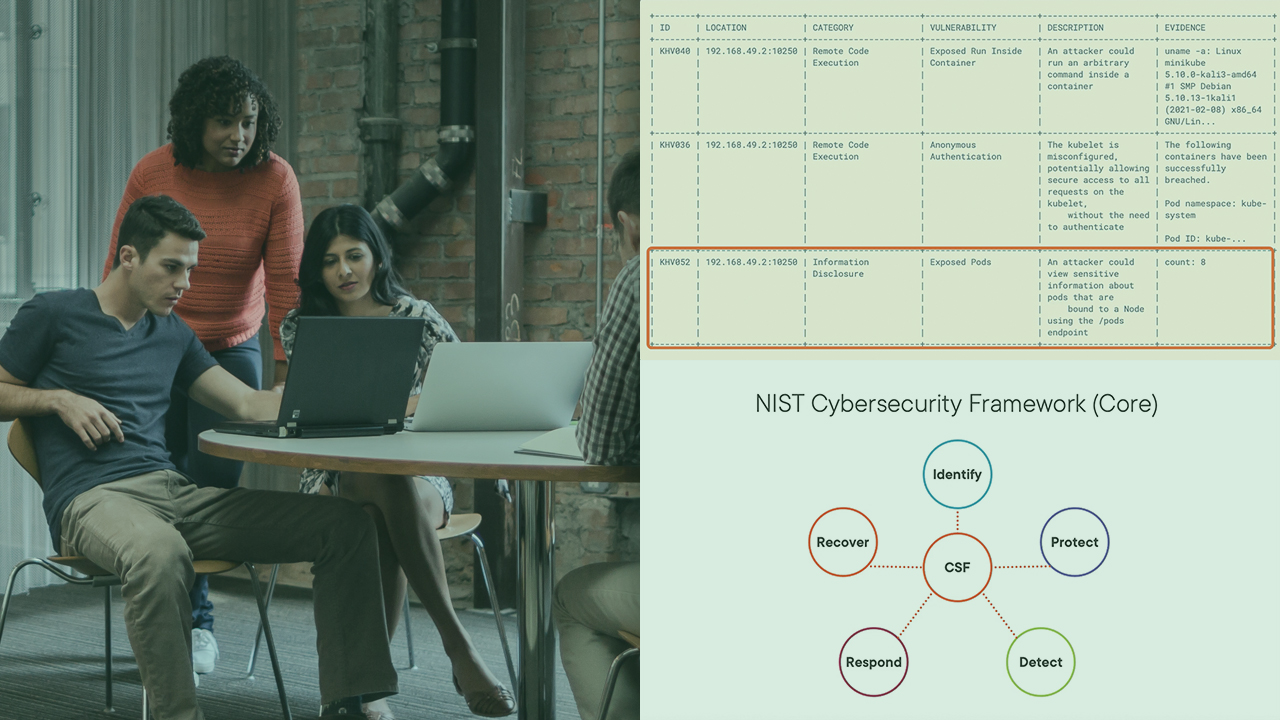
“Common” Kubernetes (K8s) hardening suggests a focus on the control plane. But what if a cluster could be backdoored through the kubelet? In this course, Container Infrastructure Analysis with kube-hunter, we will use kube-hunter to investigate a K8s attack. First, you will use kube-hunter to enumerate security weaknesses in a K8s cluster. Second, you’ll use kube-hunter findings (i.e., a discovered kubelet endpoint) to investigate privilege escalation. Third, you’ll leverage the privilege escalation findings to detect a persistence method (i.e., a malicious container image) through Trivy . Fourth, you’ll harden K8s so the aforementioned attack can’t occur again! When you’re finished with this course, you’ll have the skills and knowledge to detect these techniques: System Services (T1569), Exploitation for Privilege Escalation (T1068), and Implant Container Image (T1525).

