- Course
Credential Access with LaZagne
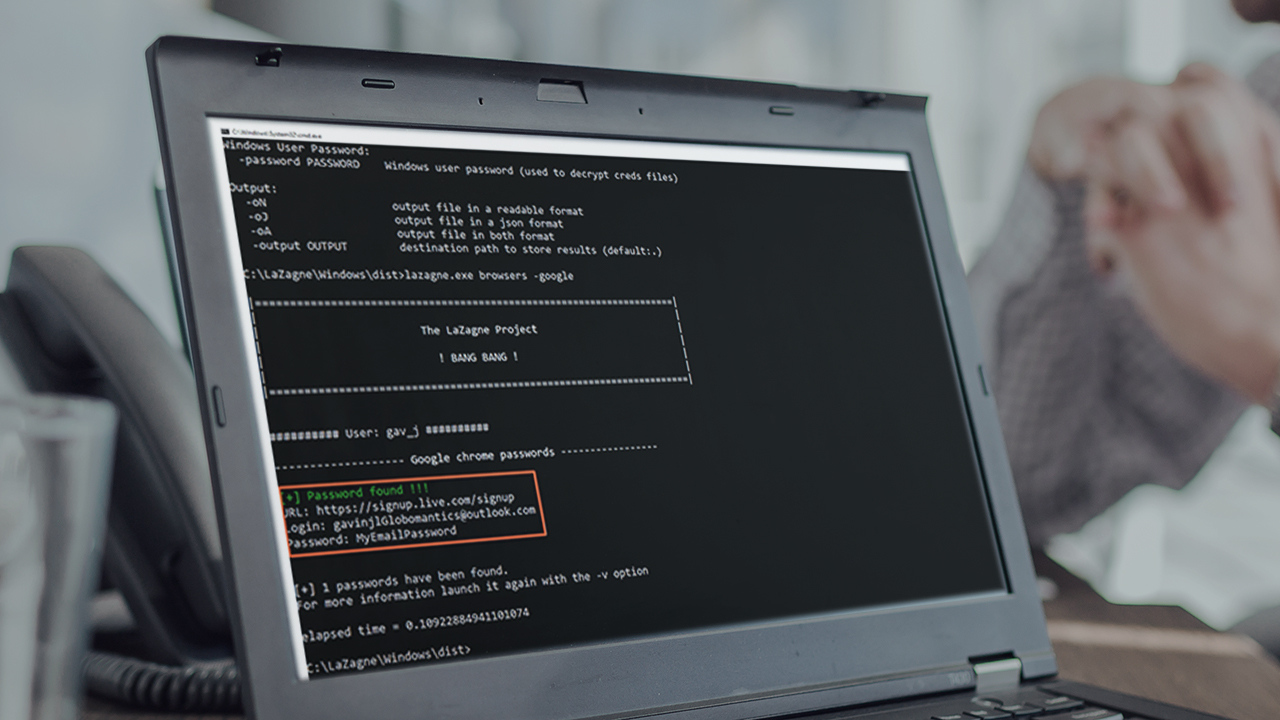
In this course, you will learn privilege escalation using LaZagne, a post-exploitation tool used to recover credentials from a system.
- Course
Credential Access with LaZagne
In this course, you will learn privilege escalation using LaZagne, a post-exploitation tool used to recover credentials from a system.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
After initial access to a system, the next goal is typically to elevate privileges and exploit further systems. LaZagne retrieves credentials from a wide variety of operating system and software sources that help to do just that. In this course, Credential Access with LaZagne, you’ll learn how to utilize LaZagne to escalate privileges in a red team environment. First, you’ll explore getting credentials stored in browsers, one of the key features of LaZagne. Next, you’ll see how to get credentials from some of the many other programs that store them on a system. Finally, you’ll learn how to get LaZagne to extract as many credentials as it can find from a system, along with how to store them in a file for easy automation. When you’re finished with this course, you’ll have the skills and knowledge to execute these techniques: Credentials from Password Stores: Credentials from Web Browsers (T1555.003) and Unsecured Credentials: Credentials In Files (T1552.001) using LaZagne. Knowing how these techniques can be used against you will ultimately lend to your ability as an organization, or an individual, to detect and defend against specific attack vectors.

