- Course
Designing and Creating Add-ons for Splunk Enterprise Security
Splunk Enterprise Security is a premium application used within the Splunk deployment to help with SOC operations. This course will teach you how to design and create add-ons to enable customization of the application and its uses.
- Course
Designing and Creating Add-ons for Splunk Enterprise Security
Splunk Enterprise Security is a premium application used within the Splunk deployment to help with SOC operations. This course will teach you how to design and create add-ons to enable customization of the application and its uses.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
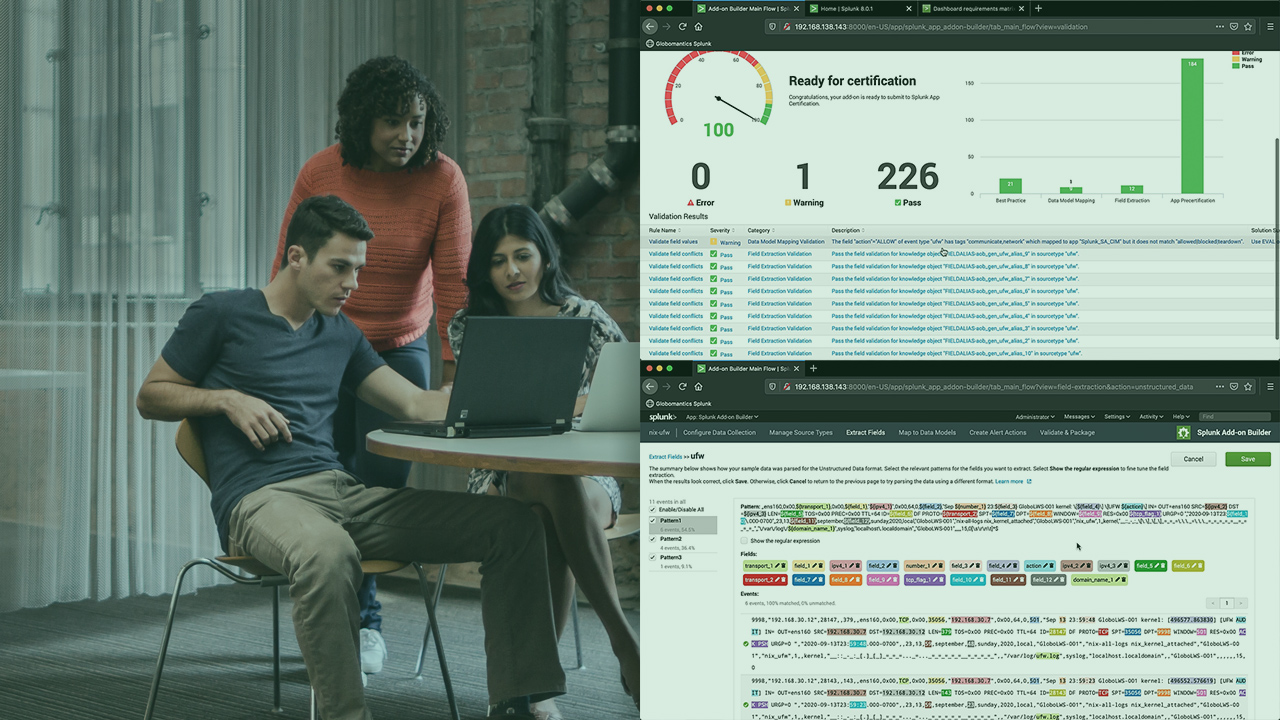
Splunk Enterprise Security (ES) solves many problems within our SOCs, including efficient operations. In this course, Designing and Creating Add-ons in Splunk Enterprise Security, you’ll learn how to design the add-on based on use cases and the data, as well as build it. First, you’ll learn about the data sources and see how to configure them for ingestion into Splunk. Next, you’ll learn about the Splunk Add-on Builder and walk through the workflow of it. We’ll design and create an add-on in Splunk. Finally, you’ll learn how to validate the add-ons to ensure that they align with best practices and recommendations. When you’re finished with this course, you’ll have the skills and knowledge of Splunk Enterprise Security needed to build add-ons for new data sources to use within Splunk Enterprise Security.
Designing and Creating Add-ons for Splunk Enterprise Security
-
Getting Ready for Splunk Data | 4m 50s
-
Understanding Data Sources for Splunk Enterprise Security | 3m 40s
-
Configuring Add-ons for Data Ingestion | 4m 57s
-
Configuring Data Sources for Splunk Enterprise Security | 7m 25s
-
Introducing the Custom Add-on Use Case | 5m 30s
-
Wrapping up the Data Discussion | 1m 26s

