- Course
Securing an EKS Cluster
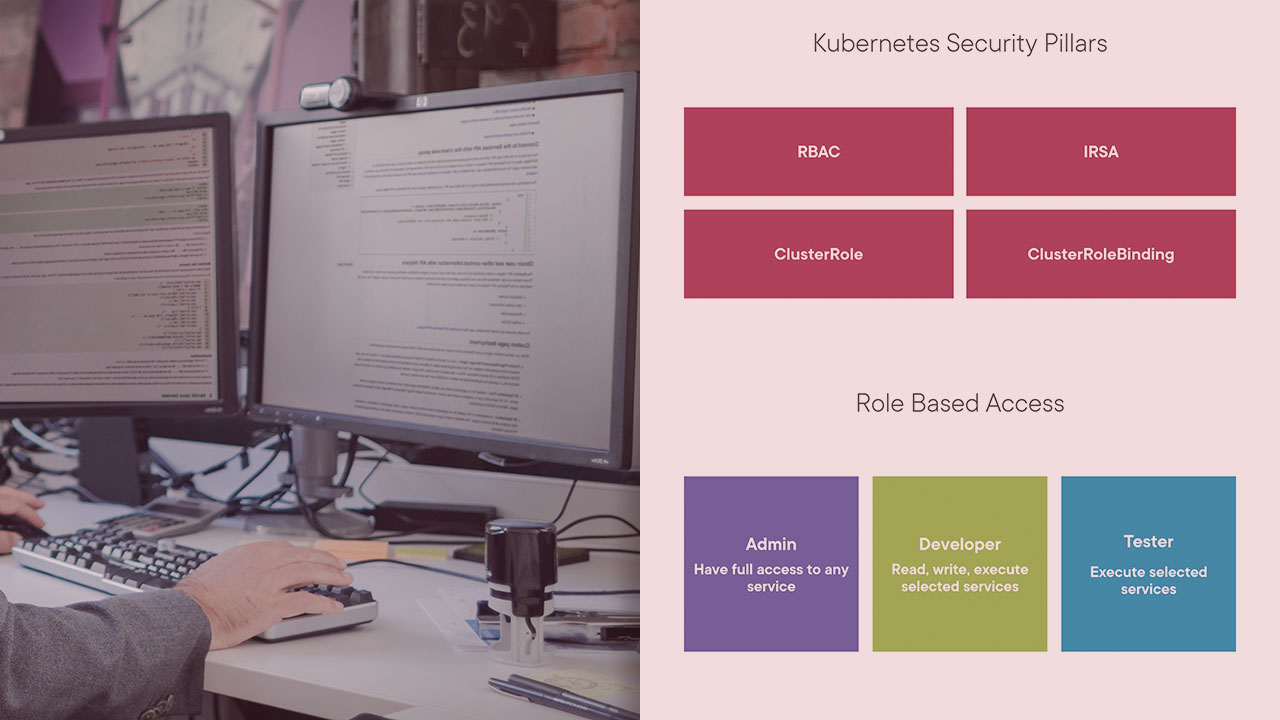
This course will teach you the security compliance concepts of the Kubernetes cluster, how to secure microservices at scale and Ensure the safety of the cluster from any security or third-party violations.
- Course
Securing an EKS Cluster
This course will teach you the security compliance concepts of the Kubernetes cluster, how to secure microservices at scale and Ensure the safety of the cluster from any security or third-party violations.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Cloud
What you'll learn
Being a DevSecOps professional you need to secure the microservices hosted on cloud or on-prem with efficient security tactics. In this course, Securing an EKS Cluster, you’ll learn to manage, secure and control microservices. First, you’ll explore Kubernetes and the administration of its cluster. Next, you’ll discover the security and IAM aspects of the Kubernetes Cluster. Finally, you’ll learn how to incorporate security and system network policies within Kubernetes. When you’re finished with this course, you’ll have the skills and knowledge of Securing Applications in Kubernetes Cluster needed to run microservices securely with the least possible privileges.

