- Course
Zero Trust Architecture (ZTA): Strategize and Establish
This course will teach you the steps involved in establishing a zero trust architecture.
- Course
Zero Trust Architecture (ZTA): Strategize and Establish
This course will teach you the steps involved in establishing a zero trust architecture.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
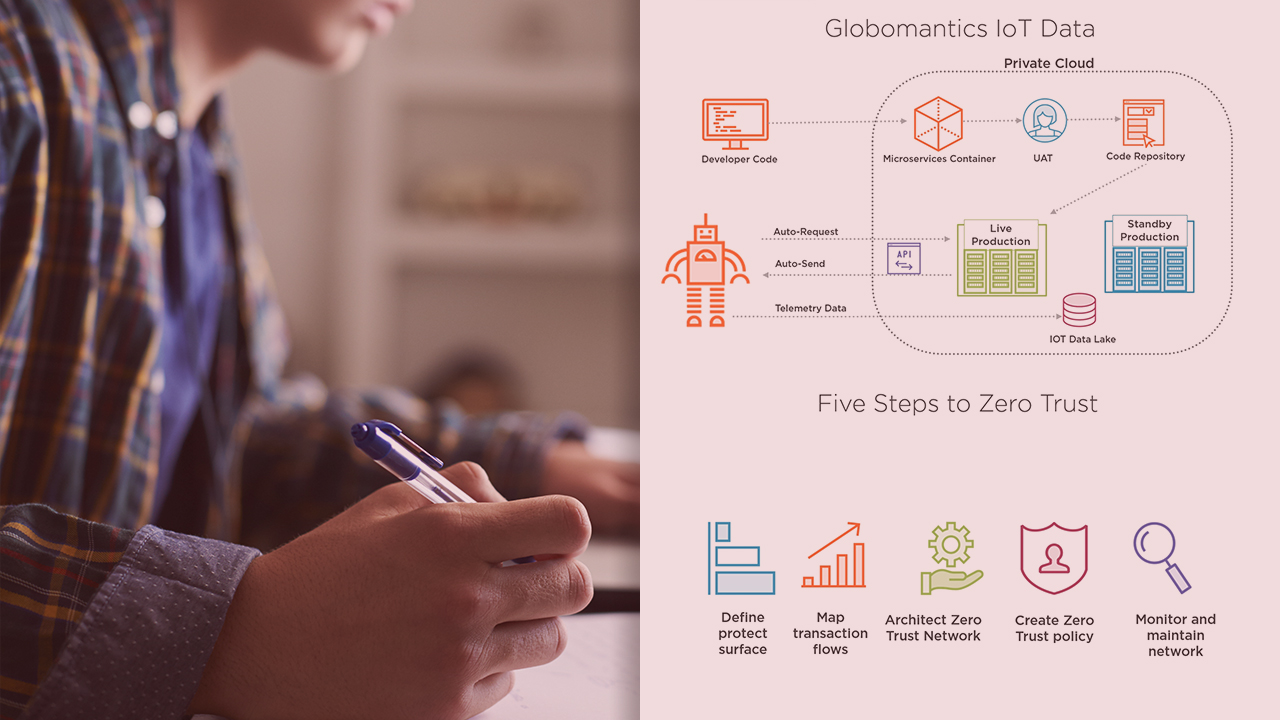
Did you know that a properly architected zero trust network removes the need for remote users to utilize corporate VPN? Zero trust architecture should be viewed as a maturing journey rather than a destination. In this course, Establishing a Zero Trust Architecture (ZTA), you’ll learn the steps you need to take on your journey. First, you’ll explore the basics of the five steps to ZTA. Next, you’ll discover identifying the business protect surface and how to capture the transaction flows. Finally, you’ll explore architecting a zero trust network, create a zero trust policy, and how to monitor and maintain your ZTA. When you’re finished with this course, you’ll have the skills and knowledge of Establishing a Zero Trust Architecture (ZTA) needed to establish your zero trust architecture.

