- Course
Getting Started with BeEF
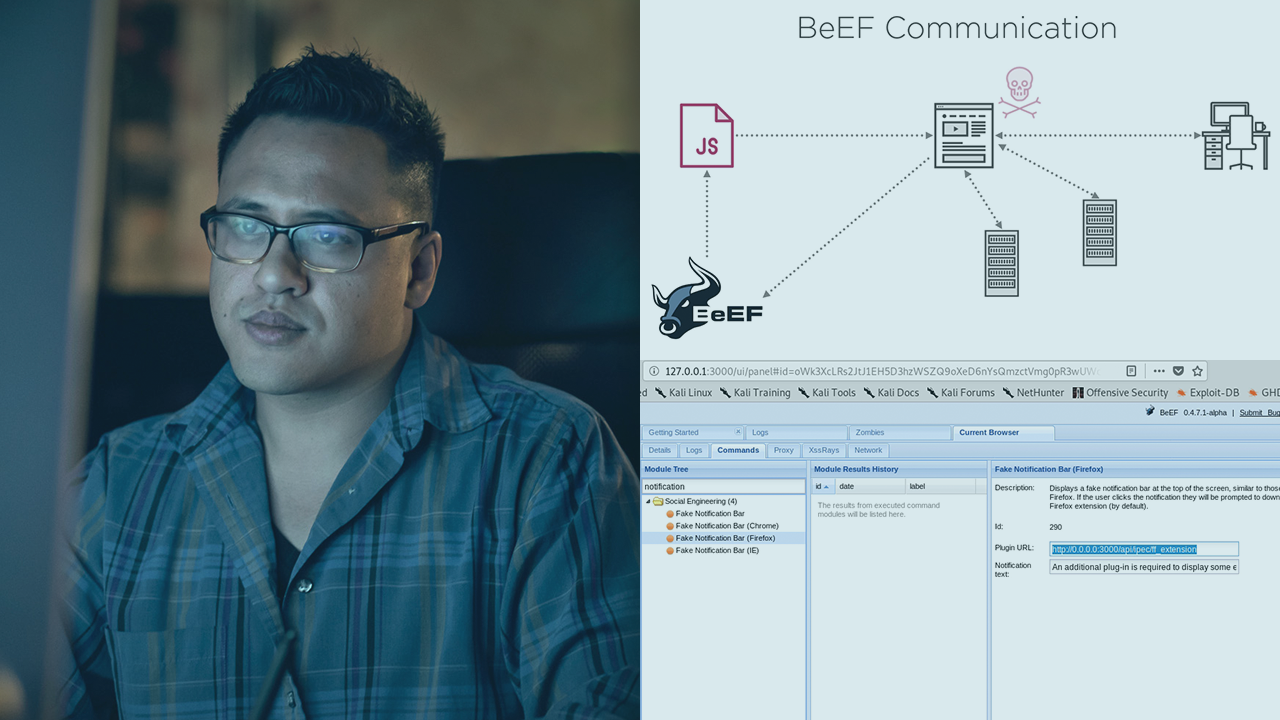
BeEF is a tool that allows cross-site scripting vulnerabilities to be investigated and exploited with minimal technical understanding. Learn how to use BeEF to exploit XSS and highlight just how critical this vulnerability can be to a website.
- Course
Getting Started with BeEF
BeEF is a tool that allows cross-site scripting vulnerabilities to be investigated and exploited with minimal technical understanding. Learn how to use BeEF to exploit XSS and highlight just how critical this vulnerability can be to a website.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Cross-site scripting (XSS) vulnerabilities can be seen as a small issue that allows an attacker to display dialog boxes and at worst steal cookies. BeEF allows us to demonstrate its importance by using XSS to demonstrate a wide variety of attacks, making it clear just how important it is to fix. In this course, Getting Started with BeEF, you will gain the ability to use BeEF to highlight how XSS can be used to highlight some of the possible effects of the vulnerability. First, you will learn about the types of XSS and how to use BeEF with the vulnerability. Next, you will discover how to maintain persistence on a machine that has been connected to our BeEF server. Finally, you will explore how to automate BeEF to allow vulnerabilities to be exploited without manual intervention. When you are finished with this course, you will have the skills and knowledge to use BeEF in a penetration test to highlight the extent to which XSS can be used against anyone who visits the affected website.

