- Course
Implement Data Auditing with Azure Data Lake
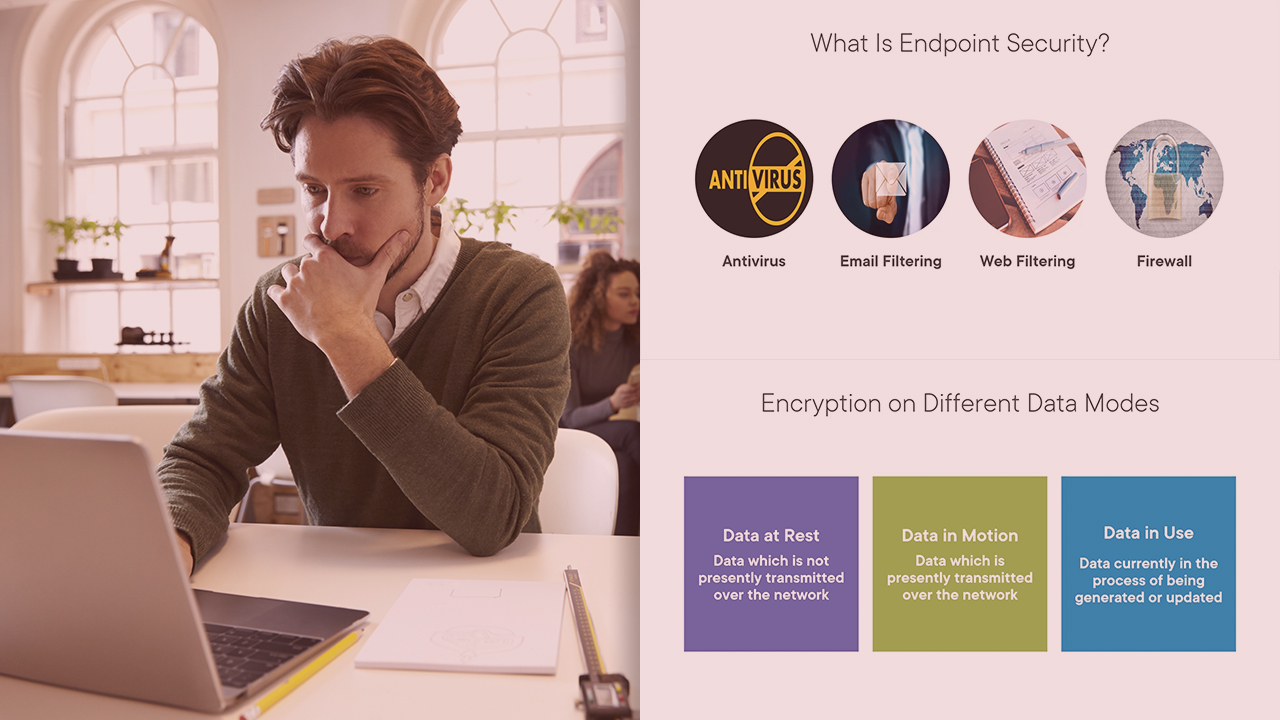
This course will teach you data auditing, data masking, and encrypting data at rest and in transit on azure cloud. Planning secure endpoints, data retention, and archiving strategy we will be implementing in place using the azure cloud portal.
- Course
Implement Data Auditing with Azure Data Lake
This course will teach you data auditing, data masking, and encrypting data at rest and in transit on azure cloud. Planning secure endpoints, data retention, and archiving strategy we will be implementing in place using the azure cloud portal.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Data
What you'll learn
Sensitive data masking should be of prime importance for efficient data governance models to be followed. In this course, Implement Data Auditing with Azure Data Lake, you’ll learn to apply efficient encryption, data masking, and secure endpoints over Azure Cloud Portal for specific services. First, you’ll explore how to design security for source data access. Next, you’ll discover designing security for data policies and standards. Finally, you’ll learn how to authenticate the service principle to mount data lake on Azure DataBricks. When you’re finished with this course, you’ll have the skills and knowledge of the importance of data masking, efficient encryption policies, management of key Vault, and policy-driven data lake architecture.

