- Course
Initial Access with King Phisher
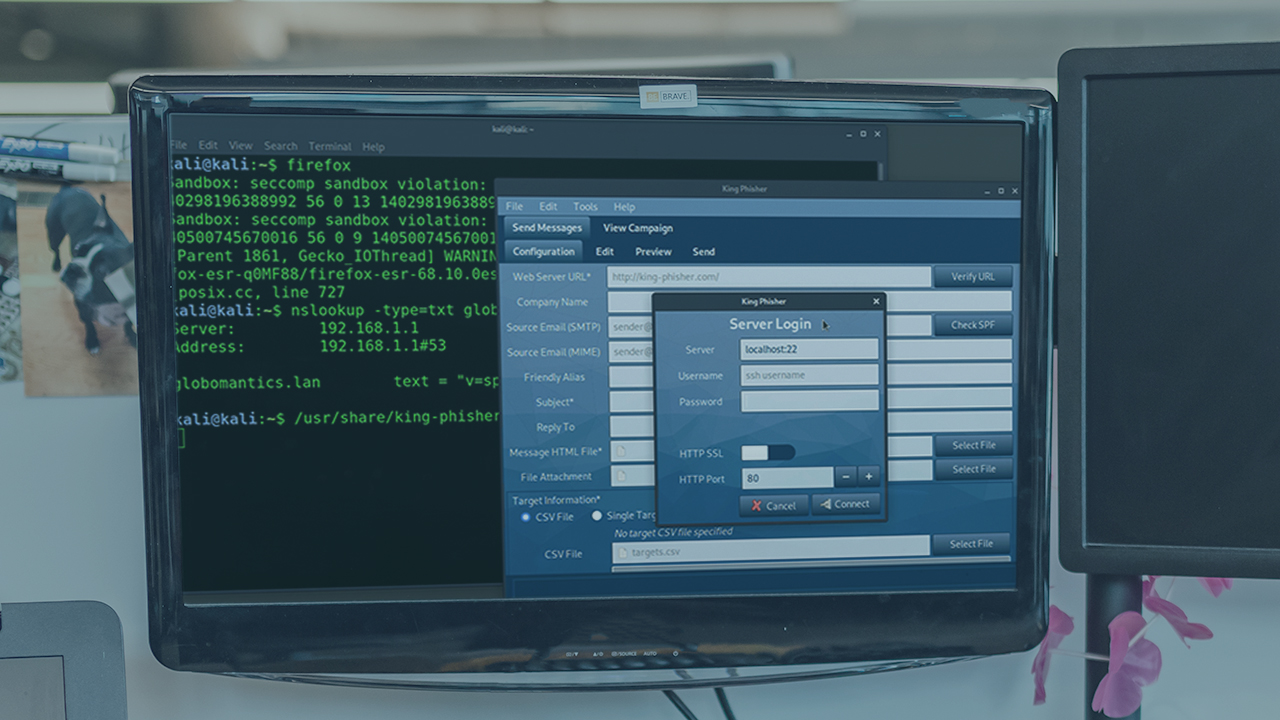
King Phisher is a feature-rich tool for coordinating and monitoring successful phishing campaigns to further red teaming objectives towards initial access. In this course, you will learn initial access using King Phisher.
- Course
Initial Access with King Phisher
King Phisher is a feature-rich tool for coordinating and monitoring successful phishing campaigns to further red teaming objectives towards initial access. In this course, you will learn initial access using King Phisher.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Through the use of phishing techniques, you'll learn the skills and understanding to further your red teaming objectives towards initial access. In this course, Initial Access with King Phisher, you’ll see how to utilize King Phisher to execute a phishing attack in a red team environment. First, you’ll demonstrate your ability to identify a victim and enumerate DNS to craft a successful phishing campaign. Next, you’ll apply a spearphishing technique to target a victim. Finally, you’ll simulate harvesting victim credentials by crafting a landing page to use in the attack. When you’re finished with this course, you’ll have the skills and knowledge to execute these techniques. Phishing: Spearphishing Link-T1566.002 & Valid Accounts-T1078 using King Phisher.

