- Course
Malware Analysis: Malicious Activity Detection
Threat actors are constantly changing their tactics and evolving their tools. This course will teach you how to create custom detections to detect and prevent emerging threats in your organization.
- Course
Malware Analysis: Malicious Activity Detection
Threat actors are constantly changing their tactics and evolving their tools. This course will teach you how to create custom detections to detect and prevent emerging threats in your organization.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
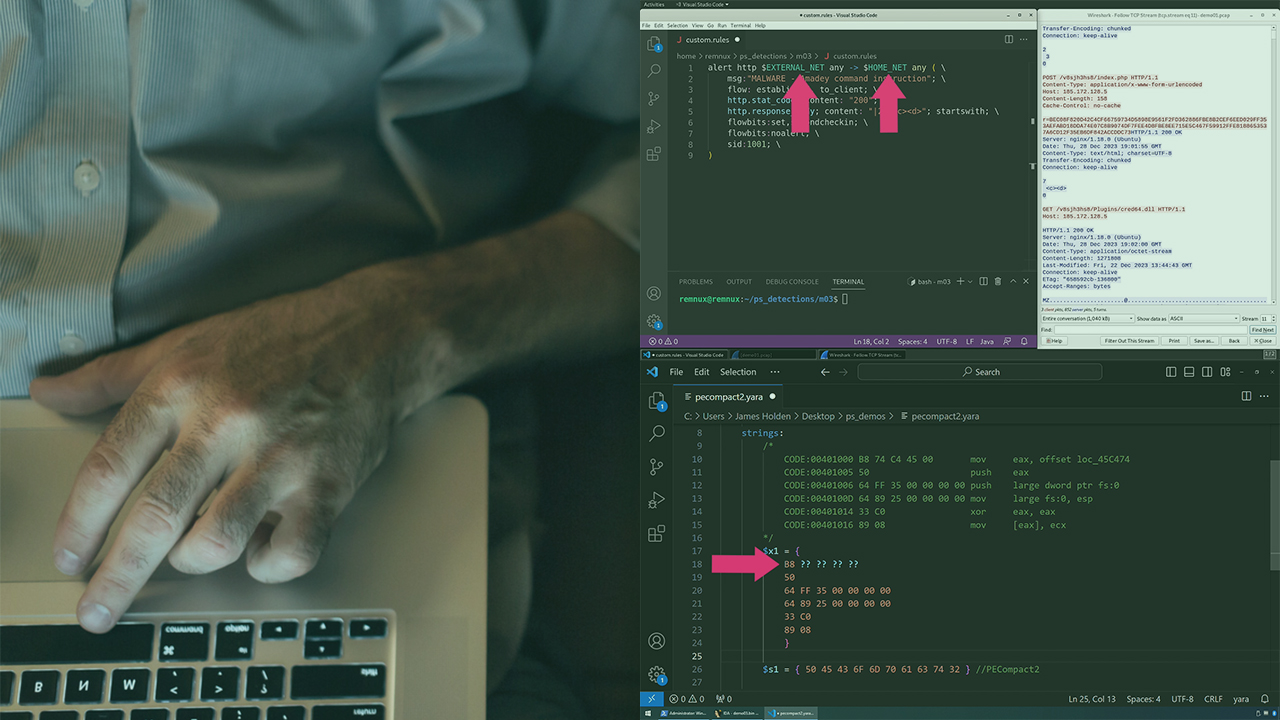
Threat actors are constantly evolving their tactics, tools, and evasion techniques. In this course, Malware Analysis, Malicious Activity Detection, you’ll learn the skills necessary to utilize this information to create custom detections with Yara, Suricata, and Sigma. First, you’ll explore the use of Yara to detect malicious files. Yara enables you to stay on the cutting edge of detecting the newest file-based threats. Next, you’ll get hands-on with Suricata creating custom rules to alert to malicious or suspicious network traffic. As most malware will need to communicate outside of your network, monitoring the network can provide valuable insight into catching malicious activity. Finally you’ll dive into Sigma to create detections from endpoint log files. This will allow you to identify malicious activity based on behavioral data from your endpoints. When you’re finished with this course you’ll have the skills and knowledge necessary to create custom detections to defend your users and your organization.

