- Course
Business Email Compromise
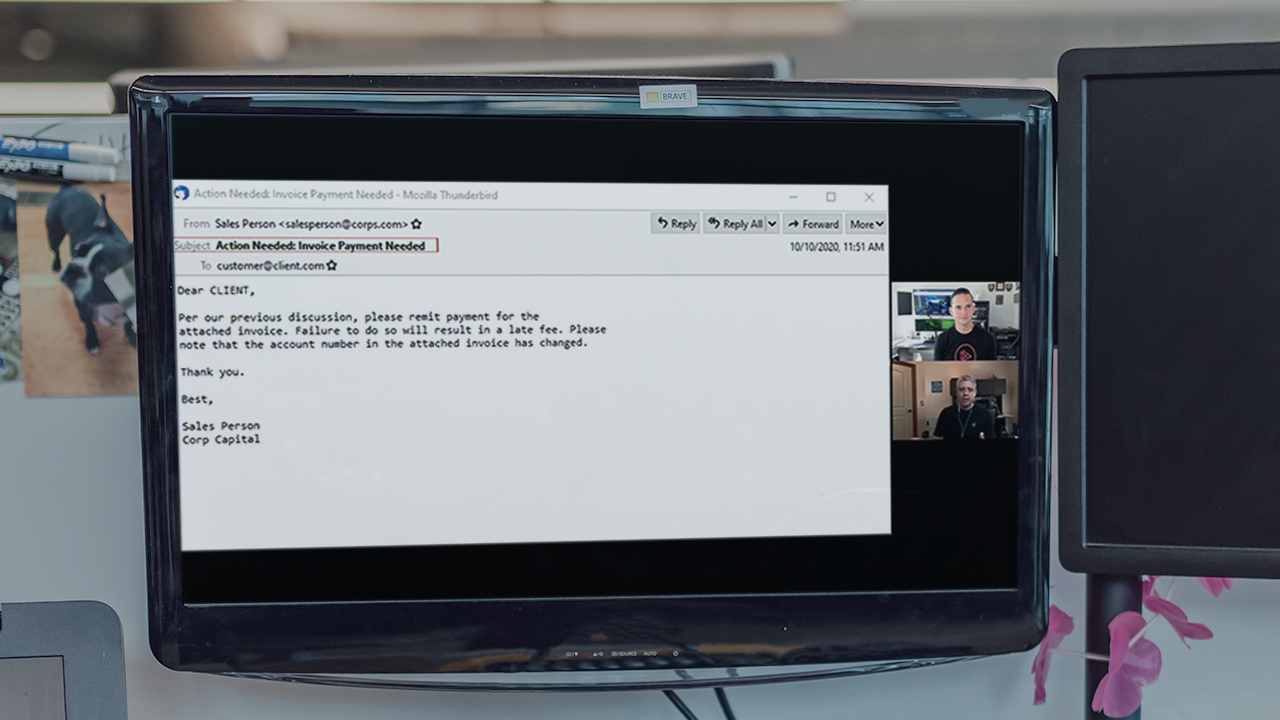
This course will teach you to prevent, detect, and when you must, respond to Business Email Compromise cyber attacks.
- Course
Business Email Compromise
This course will teach you to prevent, detect, and when you must, respond to Business Email Compromise cyber attacks.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Though not technically malware in the sense of a malicious executable running on your systems, business email compromise is just as dangerous. Leveraging the cloud based email solutions that we have come to rely on, this family of cyber attacks has become more advanced and is responsible for billions of dollars in losses. In this course, Business Email Compromise, you’ll learn how these attacks work, who they target, and various techniques attackers use to leverage email compromise access to steal money and impersonate their victims. By the end of this course, you will learn effective and practical actions you can take to prevent, detect, and if required, respond to a business email compromise attack.

