- Course
Getting Started with OAuth 2.0
OAuth 2.0 is the go-to solution for API security, bringing authorization and delegation to modern HTTP APIs. In this course, you'll learn the fundamentals of OAuth, allowing you to architect and implement the right solution for your requirements.
- Course
Getting Started with OAuth 2.0
OAuth 2.0 is the go-to solution for API security, bringing authorization and delegation to modern HTTP APIs. In this course, you'll learn the fundamentals of OAuth, allowing you to architect and implement the right solution for your requirements.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
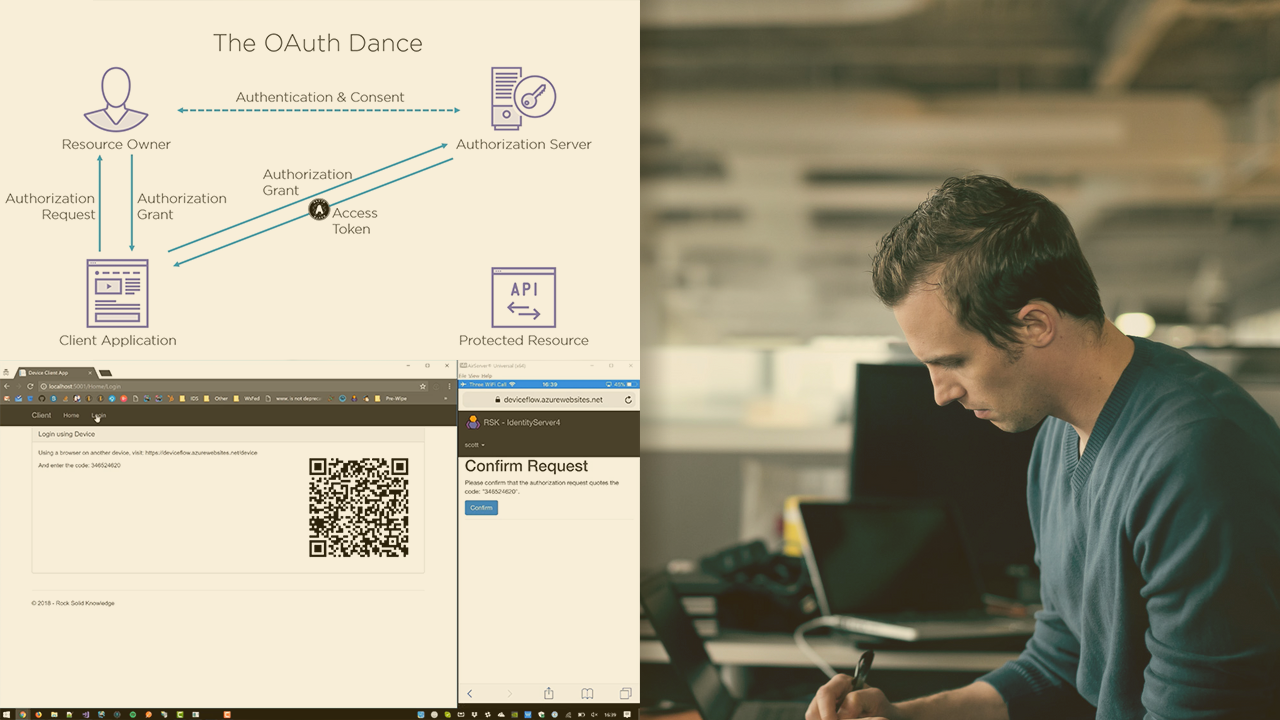
OAuth 2.0 is the go-to solution for API security, bringing authorization and delegation to modern HTTP APIs. In this course, Getting Started with OAuth 2.0, you'll learn the fundamentals of OAuth and why it is preferred over past solutions. First, you'll explore each grant type and flow in detail, looking at their strengths and weaknesses, and when they should be used or not. Next, you'll take a close look at native applications such as mobile apps, and their unique security issues when using OAuth. Finally, you'll learn some common extensions to the OAuth protocols, such as OpenID Connect and the upcoming OAuth device flow. All of this will be covered without using any particular programming language or stack. When you're finished with this course, you will know how to integrate with any OAuth 2 authorization server and architect the right solution for you.
Getting Started with OAuth 2.0
-
Version Check | 15s
-
Introduction | 1m 32s
-
A Problem of API Authorization | 2m 37s
-
A Solution: Credential Sharing | 3m 19s
-
A Solution: Cookies | 1m 6s
-
A Solution: API Keys | 2m 10s
-
The Solution: OAuth 2.0 | 5m 31s
-
Demo: A Very Typical OAuth Flow | 1m 31s
-
OAuth: A Misunderstood Protocol | 4m 42s
-
Summary | 53s

