- Course
OS Analysis with OSSEC 3
OSSEC is an opensource Host Intrusion Detection System (HIDS). In this course, you will learn OS Analysis using OSSEC.
- Course
OS Analysis with OSSEC 3
OSSEC is an opensource Host Intrusion Detection System (HIDS). In this course, you will learn OS Analysis using OSSEC.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
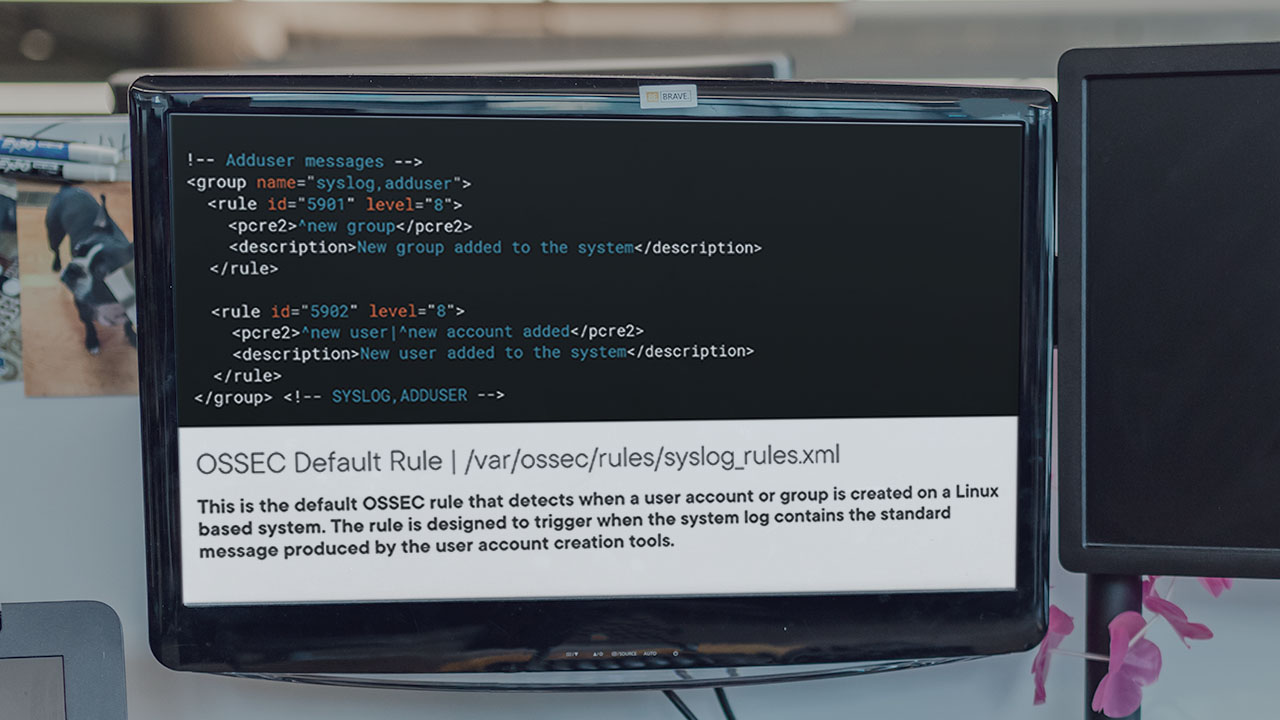
Cyber criminals often use native tools and functions of an operating system in order to perpetrate their attacks. In this course, OS Analysis with OSSEC 3, you’ll learn how to utilize OSSEC to detect authentication bypass and persistence techniques in an enterprise environment. First, you’ll learn how to detect rogue user account creation. Next, you’ll discover how accessibility features can be used for authentication bypass. Finally, you’ll analyze OSSEC logs to identify persistence using Windows scheduled tasks. When you’re finished with this course, you’ll have the skills and knowledge to detect these techniques: Create Account: Local Account T1136.001, Event Triggered Execution: Accessibility Features T1546.008, Schedule Task/Job: Scheduled Task T1053.005 using OSSEC.

