- Course
OS Analysis with Volatility
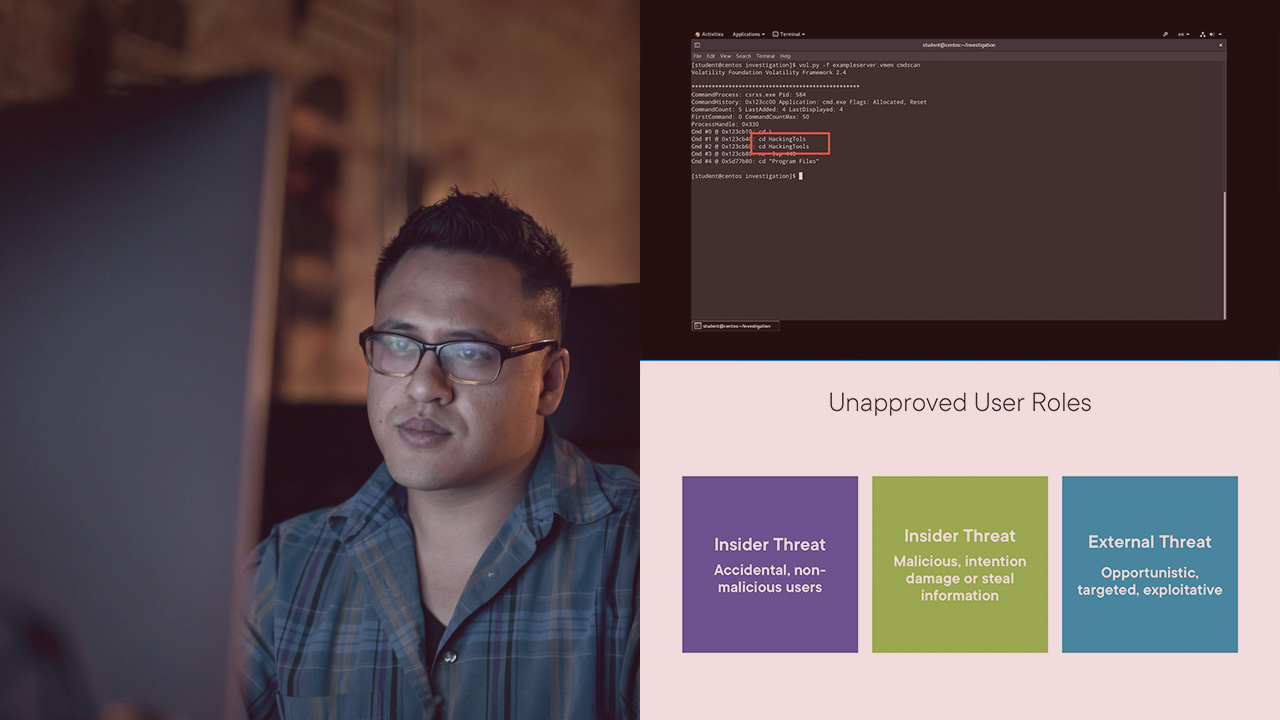
In this course, you will learn how to perform OS analysis of volatile memory using the tool volatility, the most advanced memory forensics framework.
- Course
OS Analysis with Volatility
In this course, you will learn how to perform OS analysis of volatile memory using the tool volatility, the most advanced memory forensics framework.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
In this course, OS analysis with Volatility, you will cover how to utilize Volatility to identify and detect evidence of suspected compromise such as malicious commands and programs executed on a host computer system. You will learn how to extract the command line history from the volatile memory. You will also learn how to initiate an investigation of malicious programs and how to defend against malicious program execution. When you are finished with the course, you will have the skills and knowledge to aid in mitigating technique T1055 and 1059.

