- Course
PCI DSS: Infrastructure Security
The first two requirements of PCI DSS version 3.2.1 are to build and maintain secure networks and systems. You'll learn to understand what each requirement asks for and discover practical guidance from experienced PCI assessors.
- Course
PCI DSS: Infrastructure Security
The first two requirements of PCI DSS version 3.2.1 are to build and maintain secure networks and systems. You'll learn to understand what each requirement asks for and discover practical guidance from experienced PCI assessors.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
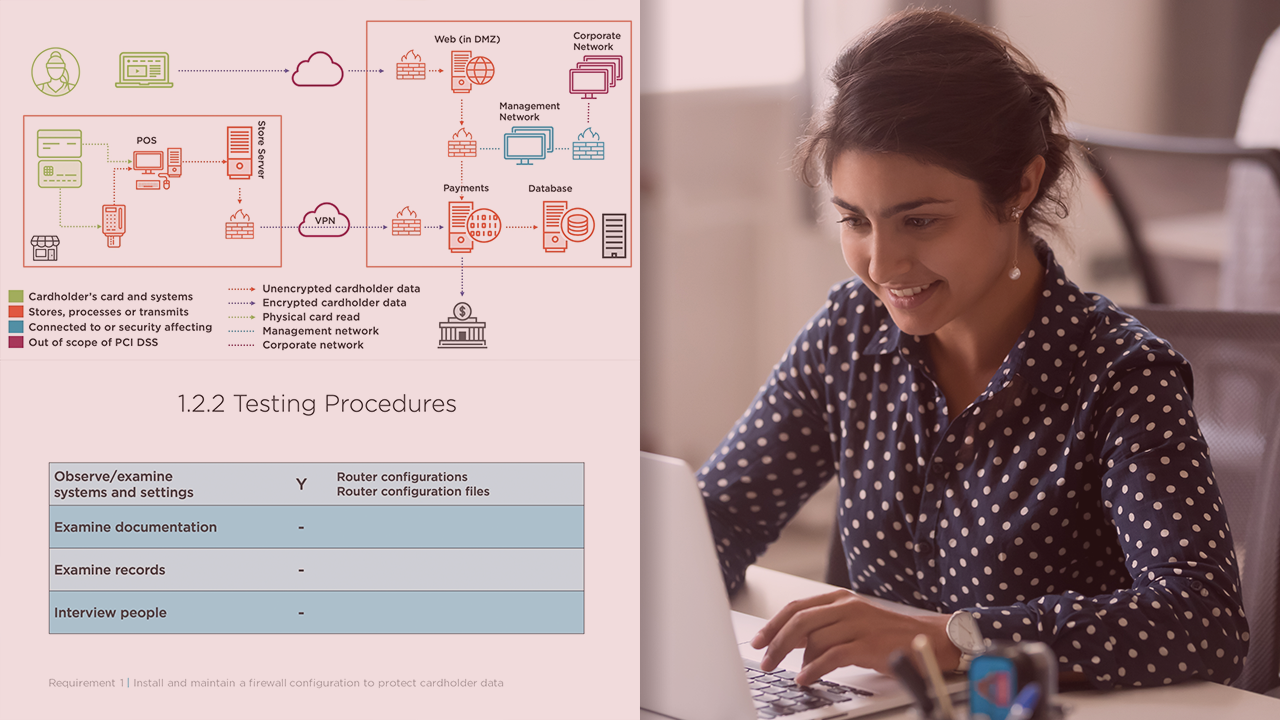
The key to achieving PCI DSS compliance is a thorough knowledge of each of the sub-requirements and how they will be assessed. In this course, PCI DSS: Infrastructure Security, you’ll learn how to interpret PCI DSS requirements 1 and 2, and apply them to your organization. First, you’ll learn how PCI DSS wants a firewall configuration to be built and maintained to protect cardholder data. Next, you’ll explore the requirement to not use vendor-supplied defaults for systems passwords and other security parameters. Finally, you’ll discover practical insights about both requirements from experienced PCI assessors. When you’ve finished with this course you will have the skills and knowledge to apply PCI DSS requirements 1 and 2 to any organization’s environment and to determine whether it is compliant with the demands of the standard.
PCI DSS: Infrastructure Security
-
Navigating the PCI DSS Standards | 5m 43s
-
1.1 Have and Implement Configuration and Management Standards | 12m 5s
-
1.2 Build and Configure Firewalls Properly | 4m 3s
-
1.3 Make All Traffic Go through a Firewall | 9m 50s
-
How Assessor Starts an Assessment of Firewalls and Network Devices | 3m 30s
-
Documenting the Business Justification for Firewall Rules | 1m 4s
-
Six Monthly Firewall Reviews | 4m 30s
-
Barriers to Achieving Compliance in Requirement 1 | 2m 21s
-
Maintain the Network Diagram | 2m 35s
-
Using Firewall Management Tools | 1m 30s
-
Typical Areas of Non-compliance and Data Compromises | 2m 29s
-
Virtual Firewalls and Firewalls in the Cloud | 2m 58s
-
What About Routers? | 2m 23s

