- Course
Software-Defined Perimeter (SDP): Leveraging Zero Trust to Create a New Network and Security Architecture
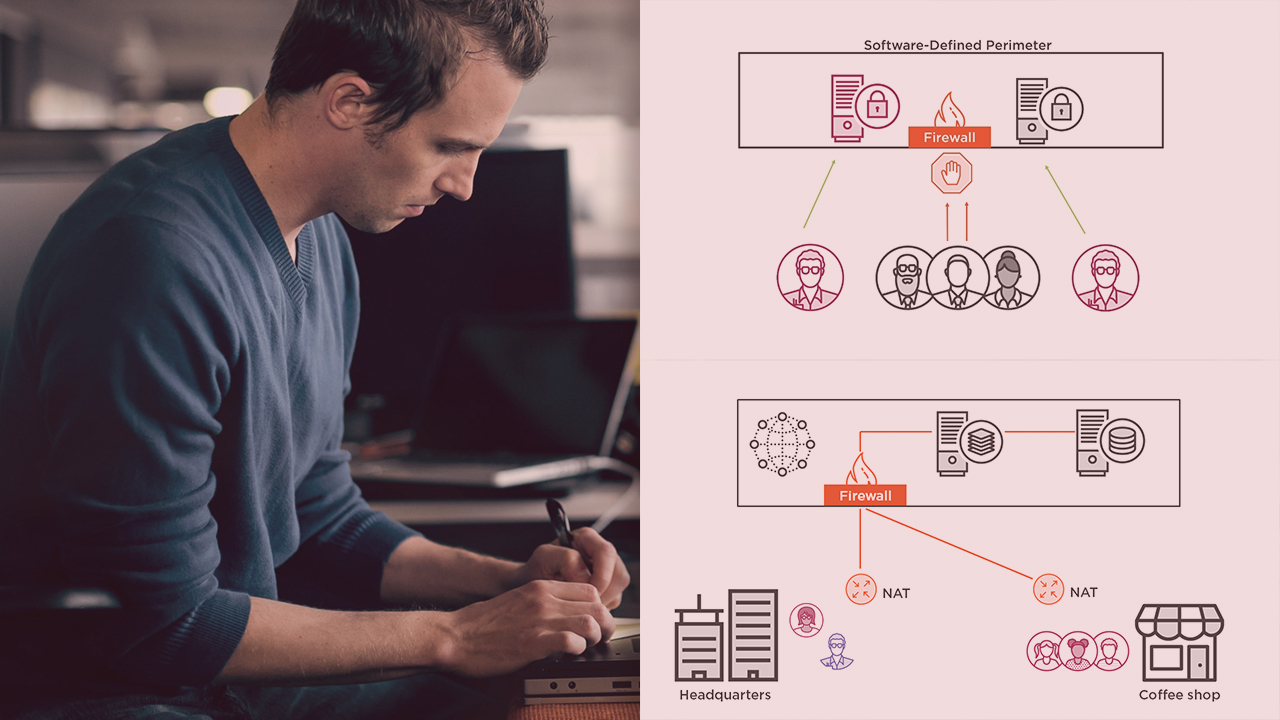
In this course, you will gain the knowledge to implement the new approach to securing your network infrastructure and applications using the software-defined perimeter approach to zero trust (SDP). SDP makes protected assets invisible.
- Course
Software-Defined Perimeter (SDP): Leveraging Zero Trust to Create a New Network and Security Architecture
In this course, you will gain the knowledge to implement the new approach to securing your network infrastructure and applications using the software-defined perimeter approach to zero trust (SDP). SDP makes protected assets invisible.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
One of today's biggest problems is that network infrastructure and applications are wide open to severe security threats.
In this course, Software-Defined Perimeter (SDP): Leveraging Zero Trust to Create a New Network and Security Architecture, you will learn foundational knowledge to protect all valuable assets from both external and internal threats.
First, you will learn why you need to adopt a zero trust software-defined perimeter. Next, you will discover the functions of a software-defined perimeter and the advantages this will bring you. Finally, you will explore how to create a software-defined perimeter.
When you're finished with this course, you will have the skills and knowledge needed to secure your infrastructure and applications from a variety of attacks that are common today.

