- Course
Secure Coding: Identifying and Mitigating XML External Entity (XXE) Vulnerabilities
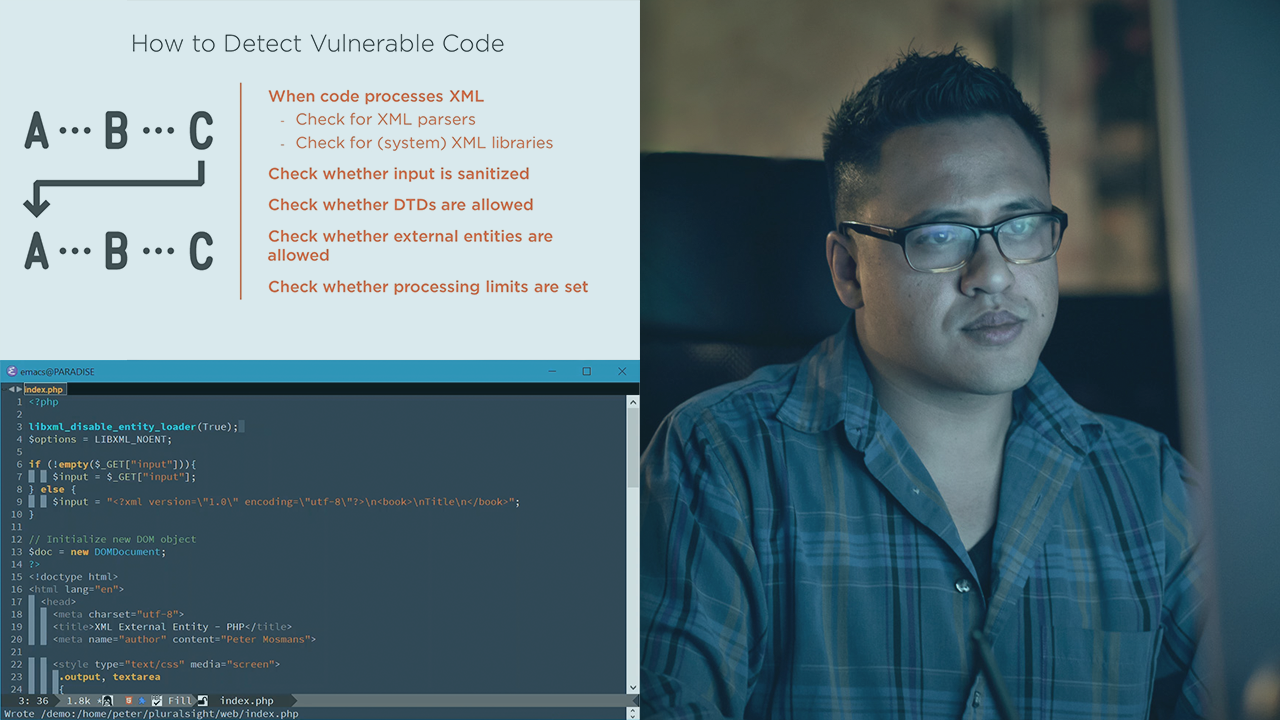
This course will teach you what XML External Entity vulnerabilities are, how they are exploited, how you can identify the vulnerabilities in your code, and how you can protect your code against exploitation.
- Course
Secure Coding: Identifying and Mitigating XML External Entity (XXE) Vulnerabilities
This course will teach you what XML External Entity vulnerabilities are, how they are exploited, how you can identify the vulnerabilities in your code, and how you can protect your code against exploitation.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
The OWASP Top 10 2017 contains a new entry; XML External Entities (XXE). As not many people know what this vulnerability is, it can be difficult to prevent against. In this course, Secure Coding: Identifying and Mitigating XML External Entity (XXE) Vulnerabilities, you will learn what this vulnerability is, how it ended up in the latest OWASP Top 10, how you can identify it in your code, and how to protect against it. First, you will discover the impact of a successful XML External Entity attack. Next, you will explore how to identify risky parts in your code base. Finally, you will learn how to mitigate against vulnerabilities. By the end of this course, you will be familiar with the risk that XML External Entities pose.

