- Course
Secure Coding: Preventing Broken Access Control
Learn how to protect your code from access control issues. You will gain an understanding of how an attacker might find and attack those vulnerabilities before building defenses into your code.
- Course
Secure Coding: Preventing Broken Access Control
Learn how to protect your code from access control issues. You will gain an understanding of how an attacker might find and attack those vulnerabilities before building defenses into your code.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
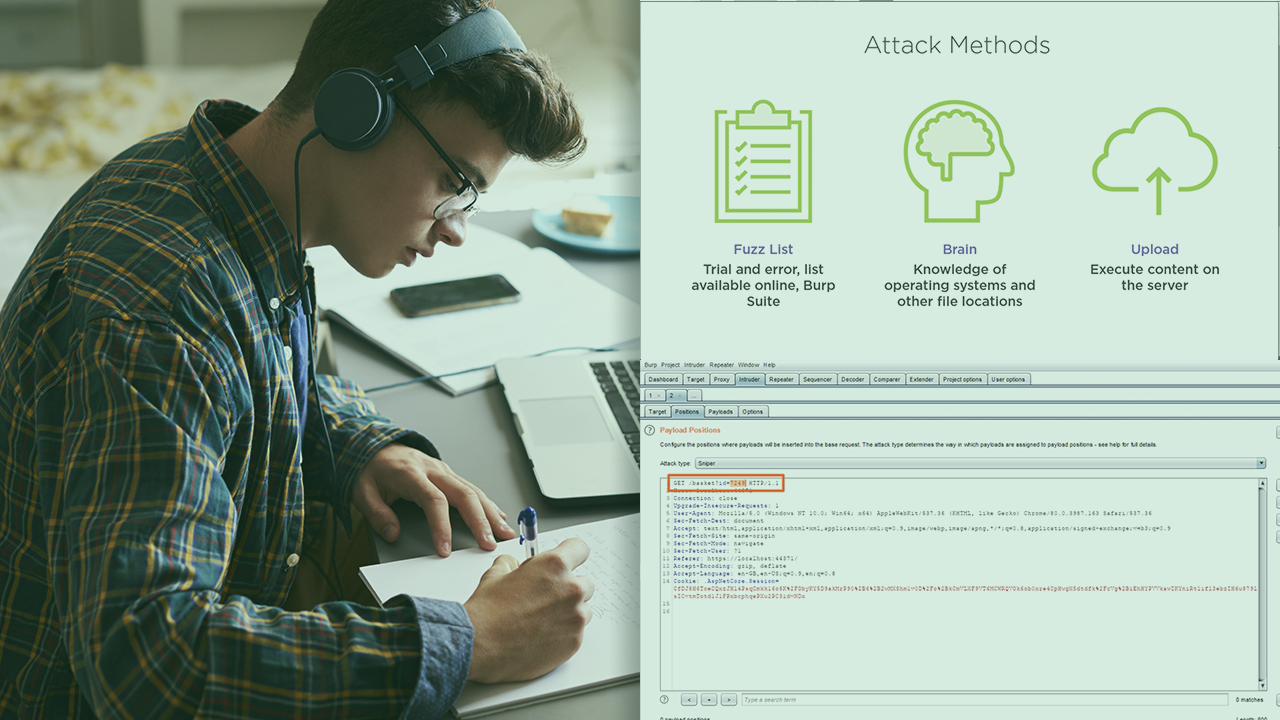
Broken access controls can expose information and functionality in your service to unauthorized users and is currently one of the top vulnerabilities found in software. You need to understand those vulnerabilities in order to defend against potential attackers. In this course, Secure Coding: Preventing Broken Access Control, you will gain the ability to protect your code from access control vulnerabilities. First, you will learn to understand vulnerabilities and potential attacks against them. Next, you will discover some of the key principles associated with defensive code. Finally, you will explore how to write clean, readable, defensive code. When you are finished with this course, you will have the skills and knowledge needed to protect your code from access control vulnerabilities.

