- Course
Security Management: A Case Study
Security management encompasses a number of verticals, dealing with the day to day, developing programs, maintaining compliance and managing risk. This course covers what's important when starting up a cyber-security initiative.
- Course
Security Management: A Case Study
Security management encompasses a number of verticals, dealing with the day to day, developing programs, maintaining compliance and managing risk. This course covers what's important when starting up a cyber-security initiative.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
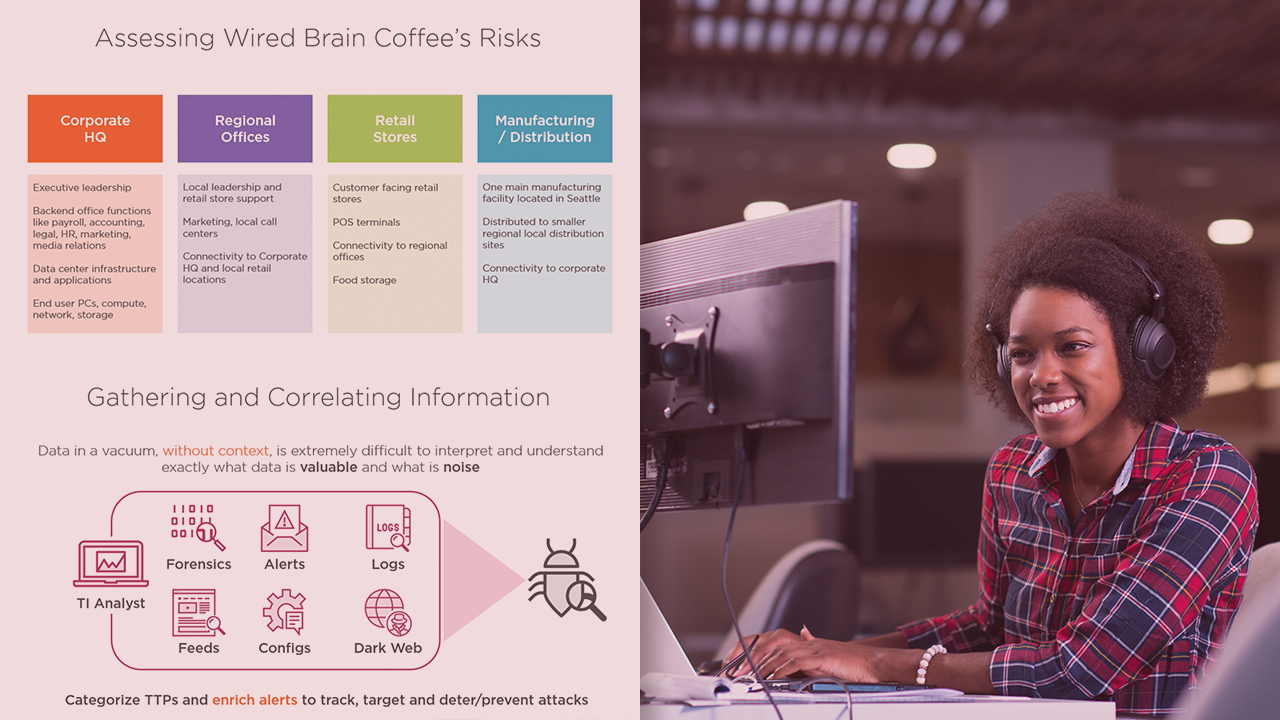
Implementing a security program can be a daunting task. There are a lot of pieces to the puzzle that must be addressed ranging from knowing what assets and data you want to protect, assessing vulnerabilities, threats and risk, to developing budgets and maintaining compliance. In this course, Security Management: A Case Study, you'll learn about defining goals, regulatory and compliance objectives, and determining risk. First, you'll review the key elements to developing a business case needed for funding a security program. Next, you'll look at defining metrics and showing ROI. Finally, you'll put the information learned throughout the Security Management Path into context When you’re finished with this course, you will have the proper context for the many skills and topics covered throughout the security management path.
Security Management: A Case Study
-
Purpose of This Course | 2m 53s
-
What's in Scope for This Course? | 2m 53s
-
The New CEO and Things to Consider | 1m 11s
-
Taking Inventory | 1m 51s
-
Business Outcomes Drive Technology Decisions | 1m 18s
-
Taking a Phased Approach | 1m 20s
-
Identify Most Critical and Work Down | 2m 27s
-
Process Should Be Focused on Security | 2m 29s
-
Capability Maturity Model | 2m 15s
-
Risk Tolerance | 41s
-
Training | 1m 27s
-
Privacy and Data Security Compliance Challenges | 4m 47s
-
Regulatory Examples | 2m 9s

