- Course
Web App Hacking: Sensitive Data Exposure
This course helps to understand various types of sensitive data exposure in modern web applications. You'll learn about testing for sensitive data exposure, common problems, and countermeasures.
- Course
Web App Hacking: Sensitive Data Exposure
This course helps to understand various types of sensitive data exposure in modern web applications. You'll learn about testing for sensitive data exposure, common problems, and countermeasures.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
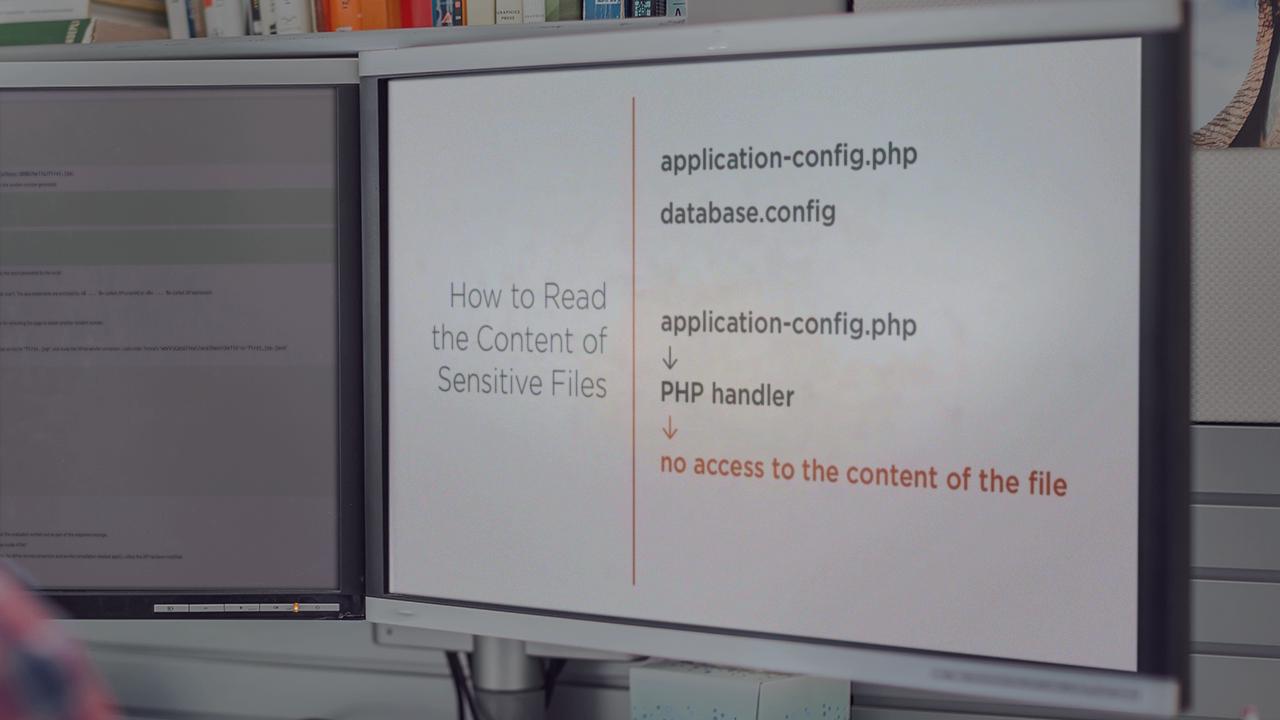
Sensitive data exposure can lead to very severe consequences (user impersonation, account takeover, disclosure of credentials – to name a few). In this course, Web App Hacking: Sensitive Data Exposure, you'll learn about various types of sensitive data exposure in modern web applications. First, you'll see how the attacker can learn the credentials to the database as a result of insecure error handling. Next, you'll learn how the attacker can read the content of sensitive files, when the files are insecurely processed. You'll also learn how to extract the metadata from publicly available files and how sensitive information can be found in metadata. After that, you'll see how easily the attacker can go from the disclosure of software version to remote code execution on the production server. Then, you'll learn about insecure communication channel between the browser and the web application. Finally, you'll learn about the disclosure of cookie with sensitive data and you'll see how the URL with sensitive information can leak to external domain via Referer header. By the end of the course, you'll know how to test web applications for different types of sensitive data exposure and how to provide countermeasures for these problems.

