- Course
SharePoint Server 2013 Core Solutions (70-331) Part 2
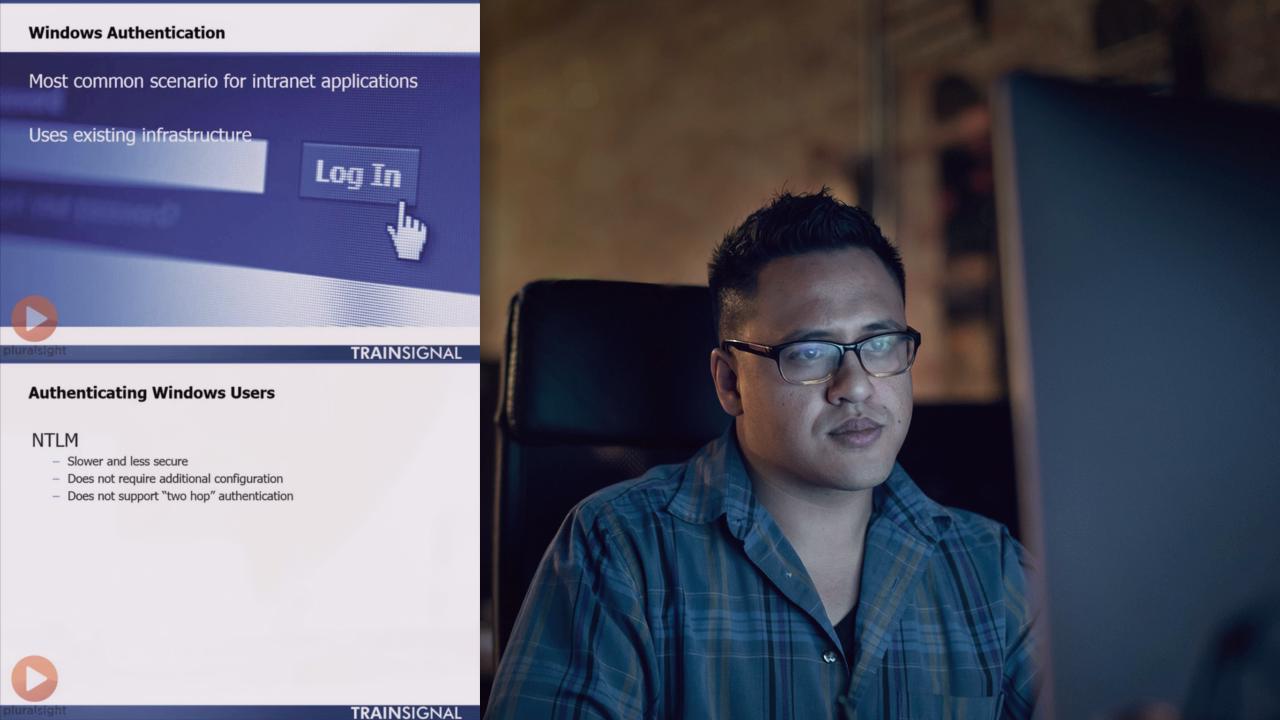
Part 2 of 3 in the SharePoint Server 2013 Core Solutions (70-331) series covers a range of topics including the installation and management of SharePoint 2013, PowerShell, data management, and more.
- Course
SharePoint Server 2013 Core Solutions (70-331) Part 2
Part 2 of 3 in the SharePoint Server 2013 Core Solutions (70-331) series covers a range of topics including the installation and management of SharePoint 2013, PowerShell, data management, and more.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
Part 2 of 3 in the SharePoint Server 2013 Core Solutions (70-331) series covers a range of topics including the installation and management of SharePoint 2013, PowerShell, data management, and more. In this course, your instructor Christopher Harrison covers a range of topics including the installation and management of SharePoint 2013, PowerShell, data management, and more. This course is designed for those who already have a basic understanding of SharePoint, Windows administration, and Active Directory concepts.

