- Course
Specialized Exploits: Stack Overflows and Bypasses
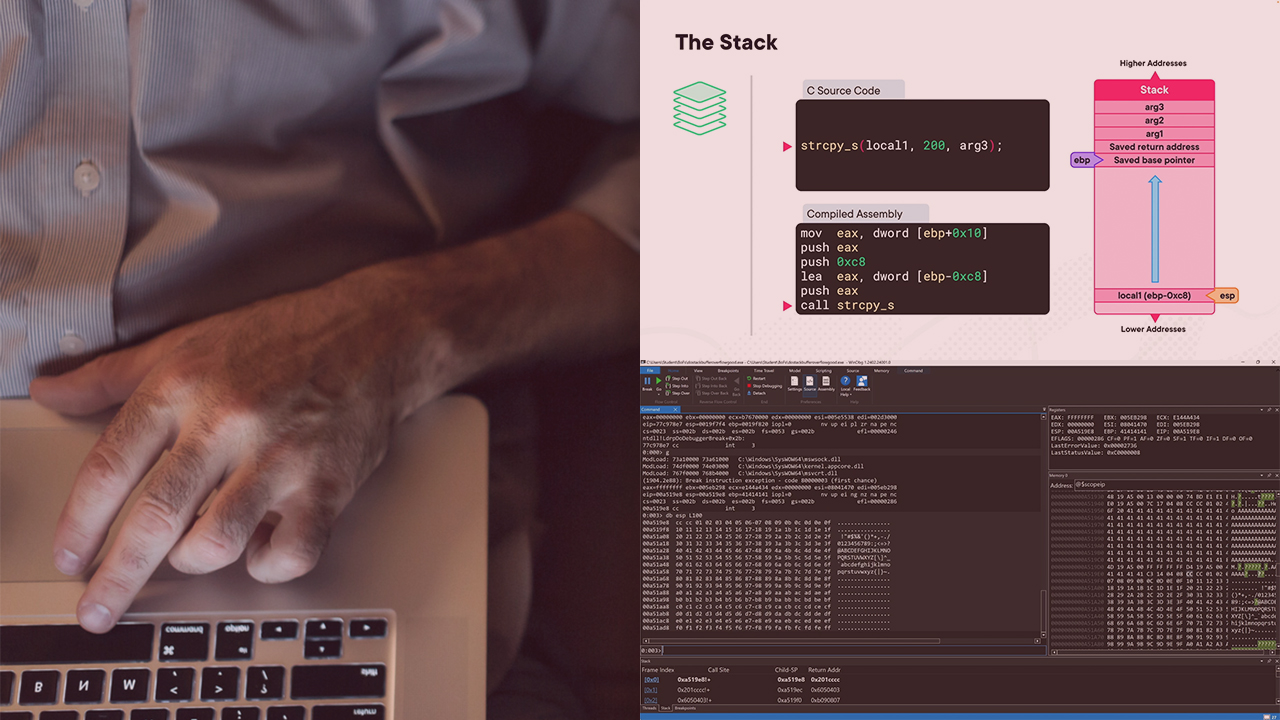
This course will teach you the essential skills required to craft Linux and Windows stack-based buffer overflow attacks.
- Course
Specialized Exploits: Stack Overflows and Bypasses
This course will teach you the essential skills required to craft Linux and Windows stack-based buffer overflow attacks.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
In the field of cybersecurity, understanding and exploiting system vulnerabilities are essential skills for professionals tasked with defending against malicious attacks. Stack-based buffer overflows, Structured Exception Handling (SEH), and stack canaries pose challenges to both defenders and attackers. This course aims to equip learners with the knowledge needed to navigate these complexities and develop effective exploit techniques. In this course, Specialized Exploits: Stack Overflows and Bypasses, you’ll learn to craft buffer overflow exploits for Linux and Windows systems. First, you’ll explore the fundamentals of stack-based buffer overflows, understanding how they occur and their impact on system security. Next, you’ll discover the intricacies of Structured Exception Handling (SEH) on Windows, learning how to exploit vulnerabilities and manipulate program execution flow. Finally, you’ll learn techniques for bypassing stack canaries on Linux, where you are introduced to methods such as stack pivoting and low entropy brute-force attacks. When you’re finished with this course, you’ll have the skills and knowledge of exploit development needed to identify, exploit, and mitigate basic vulnerabilities in software systems. Whether you're a cybersecurity enthusiast or an aspiring exploit developer, this course will empower and prepare you to tackle more complex memory corruption challenges.

