- Course
Vulnerability Management with QRadar
This course is designed to help you deploy a proper vulnerability management program using the IBM QRadar Vulnerability Management (QVM), a solution that allows you to scan your company for vulnerabilities directly from the QRadar console.
- Course
Vulnerability Management with QRadar
This course is designed to help you deploy a proper vulnerability management program using the IBM QRadar Vulnerability Management (QVM), a solution that allows you to scan your company for vulnerabilities directly from the QRadar console.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
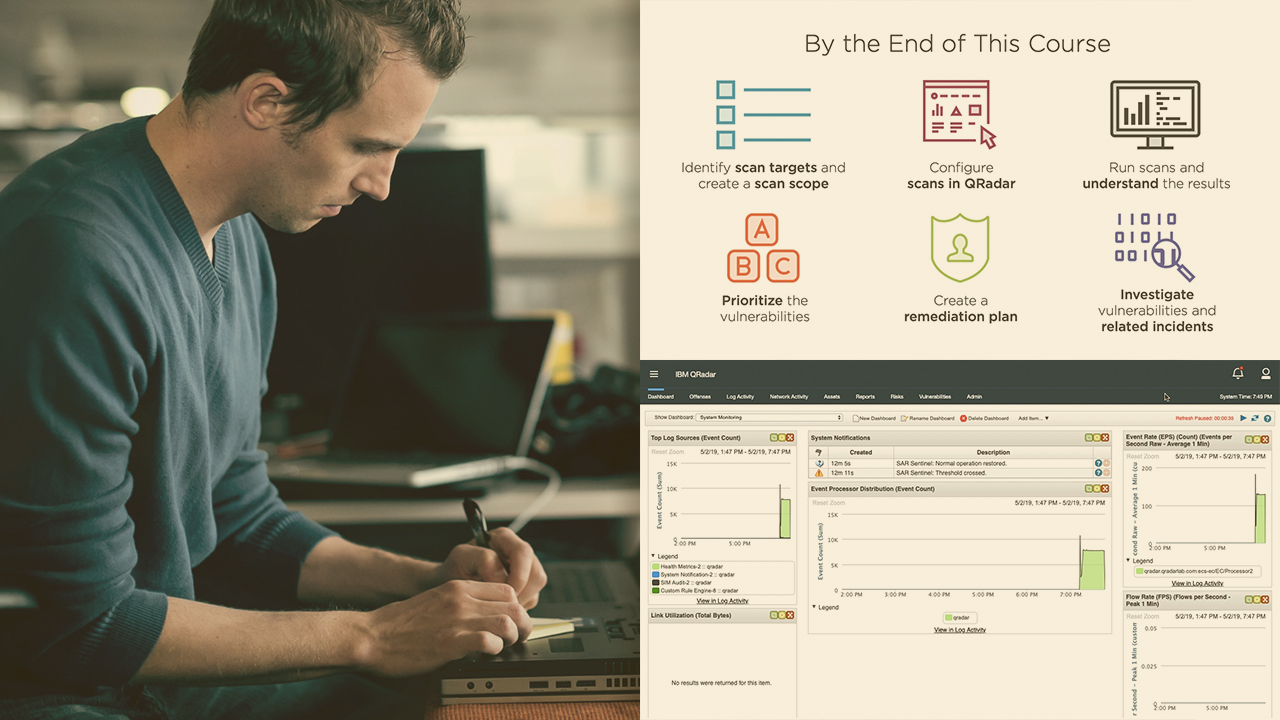
One of the main advantages of using QRadar is its variety of features in one single solution. In this course, Vulnerability Management with QRadar, you'll learn how to use the tool to detect vulnerabilities in your environment and correlate them with other information in your SIEM, such as events and flows. First, you'll learn how to identify the scope of a scan and how to work with the stakeholders to properly schedule a scan. Next, you'll be shown how to configure the scans on the tool and how to run them. Then, you'll explore the process of creating a vulnerability remediation plan, in which you'll prioritize the vulnerabilities according to your company needs. Finally, you'll discover how to investigate critical vulnerabilities and how to identify signs of exploitation. When you're finished with this course, you'll have the skills and knowledge of QVM needed to implement and run a vulnerability management program in your IBM QRadar environment.

