- Course
Web Application Penetration Testing: Information Gathering
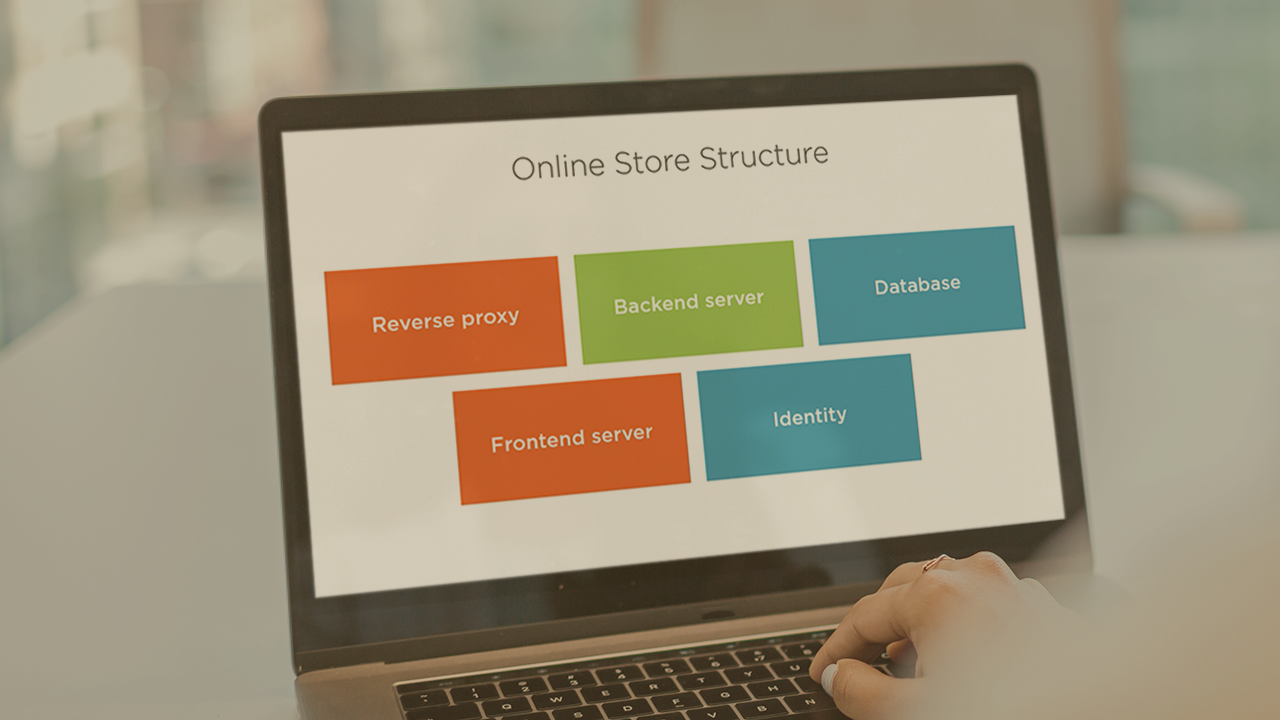
This course will teach you about web application information gathering which you can use to craft your defenses, since a web application is only as strong as its weakest link.
- Course
Web Application Penetration Testing: Information Gathering
This course will teach you about web application information gathering which you can use to craft your defenses, since a web application is only as strong as its weakest link.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
How can you prevent attacks if you don't know your enemy? In this course, Web Application Penetration Testing: Information Gathering, you’ll learn to better know how your enemies target you. First, you’ll explore fingerprinting web applications and their building blocks. Next, you’ll discover enumerating those applications and knowing their entry points. Finally, you’ll learn how to use all the needed tools. When you’re finished with this course, you’ll have the skills and knowledge needed to understand how information can be gathered about web targets.

