- Course
Web API v2 Security
Implementing Authentication and Authorization in ASP.NET Web API v2.
- Course
Web API v2 Security
Implementing Authentication and Authorization in ASP.NET Web API v2.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
The main feature focus of ASP.NET Web API v2 was security. There's a brand new authentication system and support for popular authentication methods, like OAuth2 tokens, that is already built-in. Additionally, it is now much easier to use Web APIs from JavaScript clients and the new security extensibility gives you powerful features to integrate your APIs in arbitrary security systems.
Web API v2 Security
-
Overview | 39s
-
Transport Security | 2m 54s
-
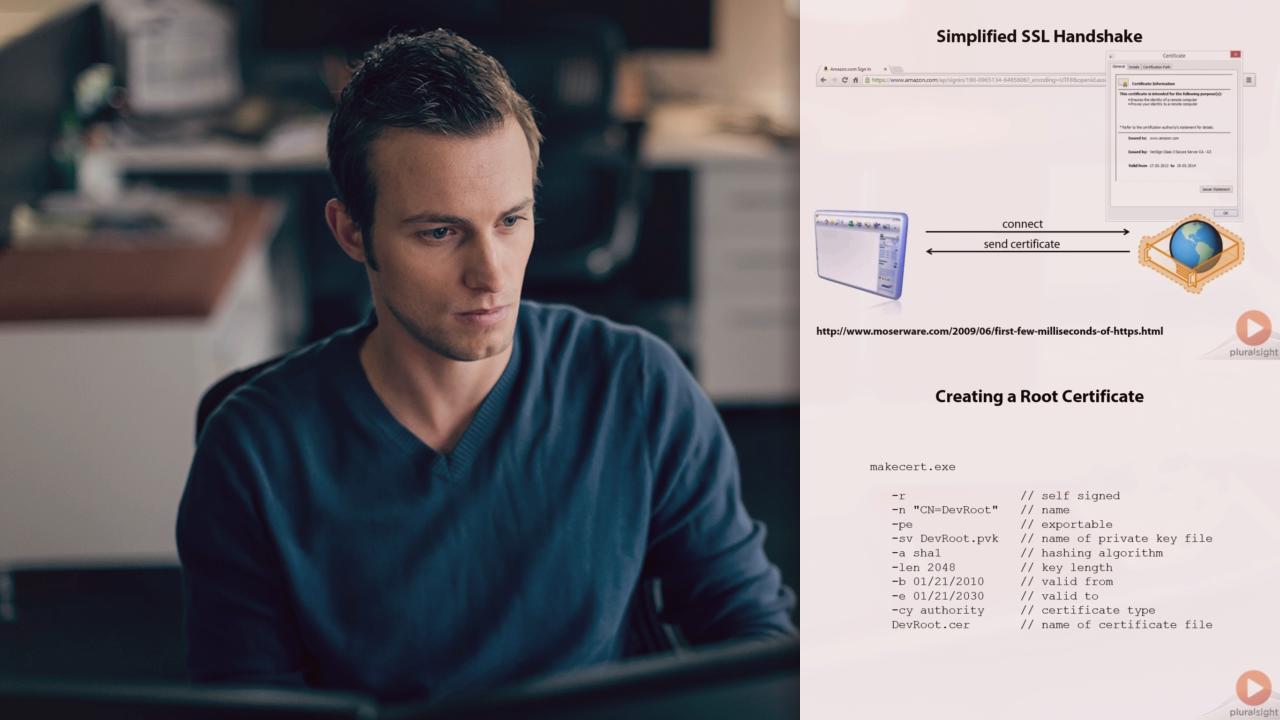
X.509 Certificates | 2m 6s
-
SSL Handshake | 3m 47s
-
Developers and SSL | 3m 57s
-
Where to get Certificates from? | 3m 20s
-
Creating Certificates | 2m 48s
-
Demo: Building an SSL Development Environment | 17m 29s
-
Demo: Command Line Tools and Self-hosting | 7m 8s
-
Demo: Fiddler and SSL Tracing | 6m 8s
-
Validating Certificates using .NET APIs | 16m 6s
-
Resources | 1m 8s

