- Course
Writing Zeek Rules and Scripts
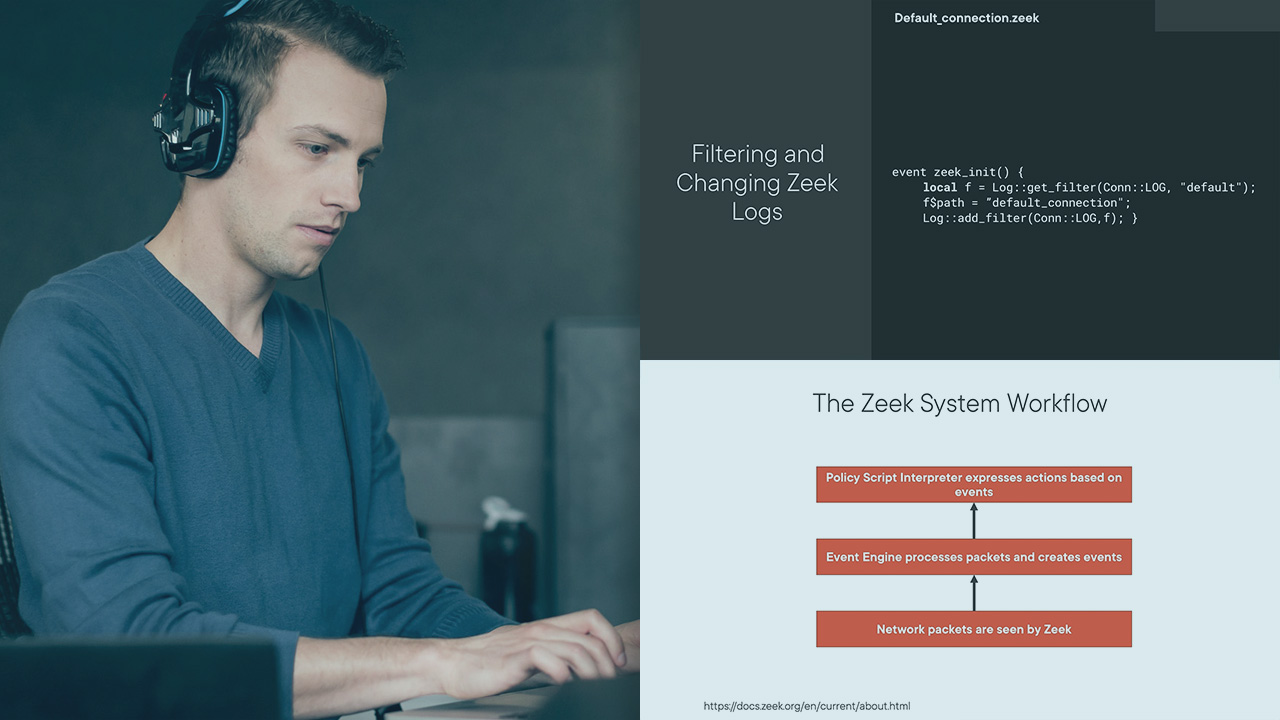
Zeek is a customizable, open-source tool that allows you to monitor the network and analyze events within it. This course will teach how to customize it through the use of custom rules, scripts, and policies.
- Course
Writing Zeek Rules and Scripts
Zeek is a customizable, open-source tool that allows you to monitor the network and analyze events within it. This course will teach how to customize it through the use of custom rules, scripts, and policies.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Zeek is an event-based network monitoring and analysis tool used to help monitor the network and detect potential threats. It enables users to see the traffic going through our networks and respond to it in different ways. Learning how to customize its functionality through the use of rules and scripts can help you use this tool more effectively. In this course, Writing Zeek Rules and Scripts, you will learn all about this tool's frameworks and how to use them to customize the tool, as well as how to use it. First, you will learn about the various components used with Zeek customization and scripting. Next, you will learn about the Default scripts and how to modify them to suit your needs. Finally, you will practice using the frameworks to build the needed functionality for your use cases. When you're finished with this course, you will have the ability to modify Zeek in order to support your desired use cases and environment.

