- Course
Securing Spring Data REST APIs
If you got a text from an unlisted number asking for your credit card, would you give it out? Actually, we do this with customer data all the time in our REST APIs. Learn how Spring Security simplifies OAuth 2.0 and helps close these security gaps.
- Course
Securing Spring Data REST APIs
If you got a text from an unlisted number asking for your credit card, would you give it out? Actually, we do this with customer data all the time in our REST APIs. Learn how Spring Security simplifies OAuth 2.0 and helps close these security gaps.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
REST APIs need to be good data stewards. To achieve that, it is fundamental to know who is asking you for data and whether their request is authorized. Spring Security is here to help. In this course, Securing Spring Data REST APIs, you will gain the ability to authenticate and authorize REST APIs in Spring. First, you will learn where HTTP Basic is helpful and not so helpful. Next, you will discover OAuth 2.0 and Bearer Token Authentication using JWTs and Opaque tokens, and how to map these to granted authorities. Finally, you will explore how to manage token ingress and egress using CORS, BFF, API Gateway, and other patterns. When you are finished with this course, you will have the skills and knowledge of Spring Security needed to secure REST APIs.
Securing Spring Data REST APIs
-
Broken Ziplines and OWASP | 54s
-
Carol Meets Spring Security | 1m 8s
-
A New Year's Resolutions REST API | 31s
-
Hello Spring Security for REST APIs | 56s
-
Did We Lock Ourselves Out? | 1m
-
UserDetailsService and REST APIs | 1m 10s
-
Using InMemoryUserDetailsManager | 1m 36s
-
Introducing JdbcUserDetailsManager | 1m 28s
-
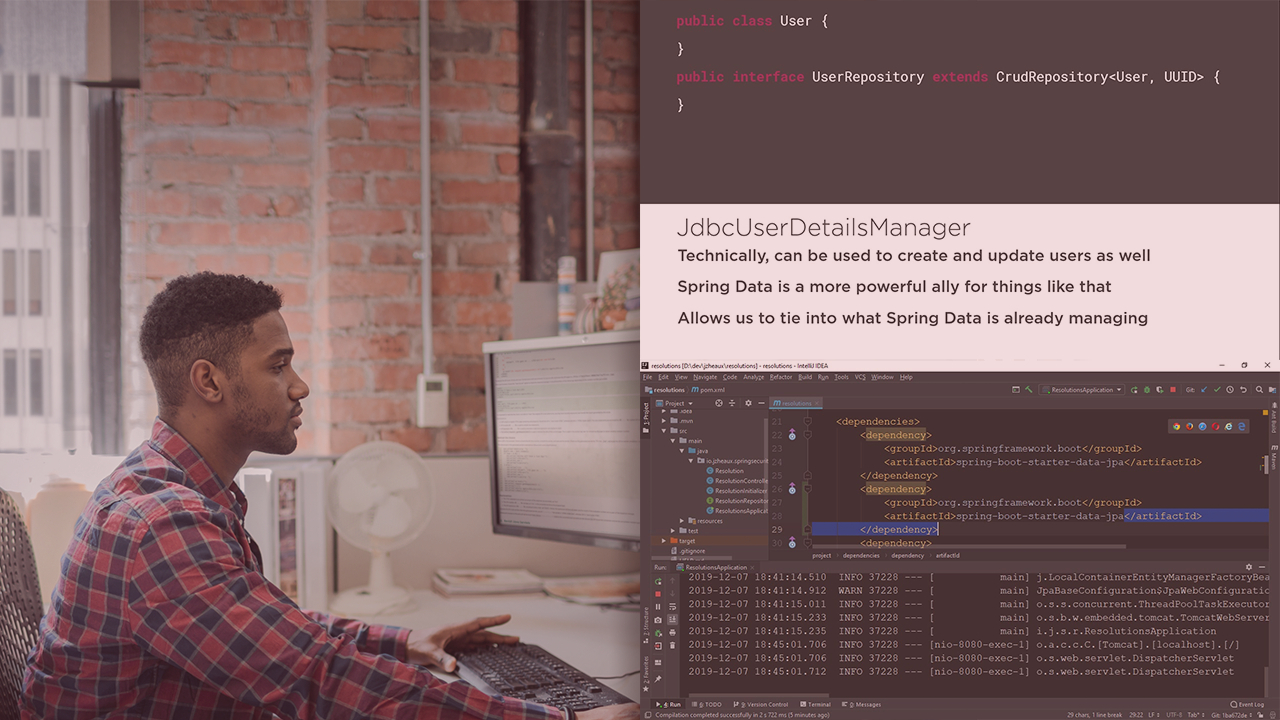
Integrating JdbcUserDetailsManager with Spring Data | 3m 16s
-
Adding Roles via Spring Data | 31s
-
Integrating JdbcUserDetailsManager with Spring Data, Part II | 3m 4s
-
Evaluating UserDetailsService Implementation Needs | 35s
-
Creating a Custom Implementation | 3m 39s
-
How Secure Is This? | 2m 44s

