- Course
CompTIA Security+ (SY0-401) Access Control and Identity Management
This course covers domain 05 of the CompTIA Security+ SY0-401 certification exam. This course deals with controlling user access and identity management tools and techniques.
- Course
CompTIA Security+ (SY0-401) Access Control and Identity Management
This course covers domain 05 of the CompTIA Security+ SY0-401 certification exam. This course deals with controlling user access and identity management tools and techniques.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
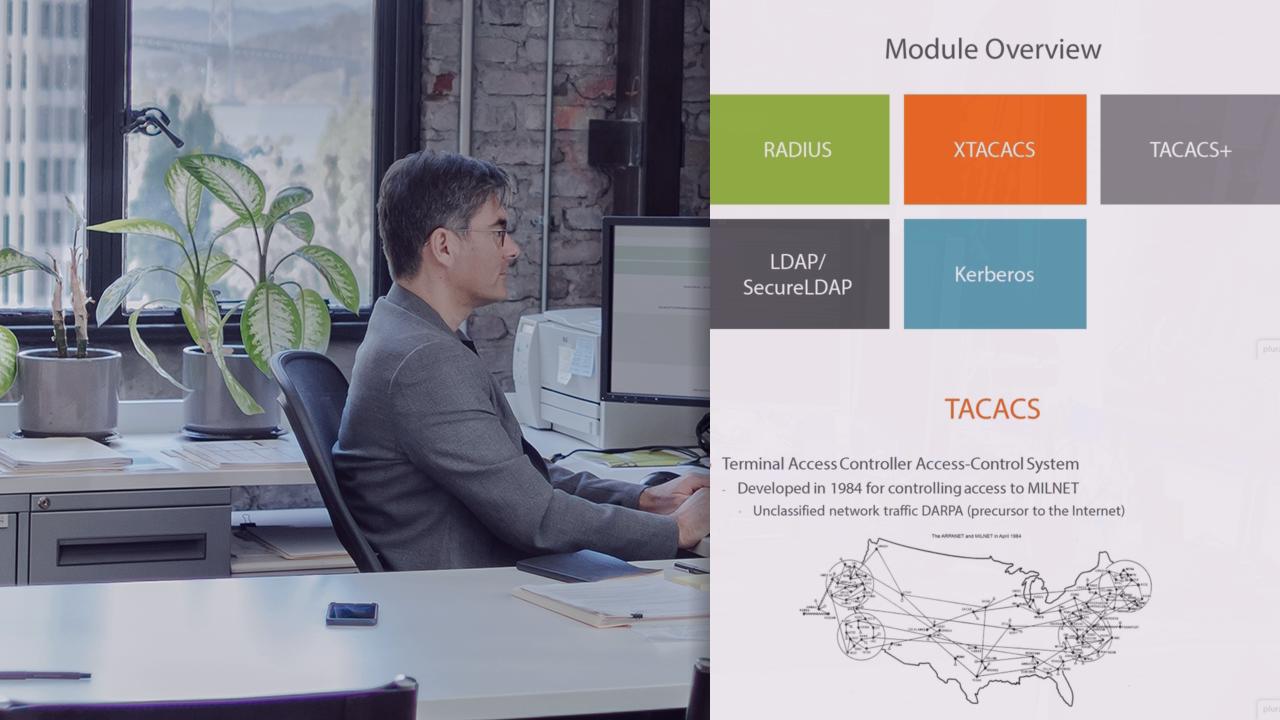
Access control and identity management is crucial to maintaining and secure environment. Various hardware controls like RADIUS, TACACS+ and XTACACS are covered, along with directory services and authentication services like Kerberos, LDAP, SAML, and Secure LDAP. The differences between identification, authentication, and authorization are covered, along with the various tools used to ensure users are connected securely with access to resources they need. Technologies and concepts including tokens, multi-authentication, TOTP, HOTP, CHAP, and PAP are covered, along with authentication factors.

