- Course
Web App Hacking: Cookie Attacks
In this course, you will learn how severe consequences can happen as a result of insecure cookie processing. You will see how cookie attacks work in practice and how to test web applications for various cookie processing flaws.
- Course
Web App Hacking: Cookie Attacks
In this course, you will learn how severe consequences can happen as a result of insecure cookie processing. You will see how cookie attacks work in practice and how to test web applications for various cookie processing flaws.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
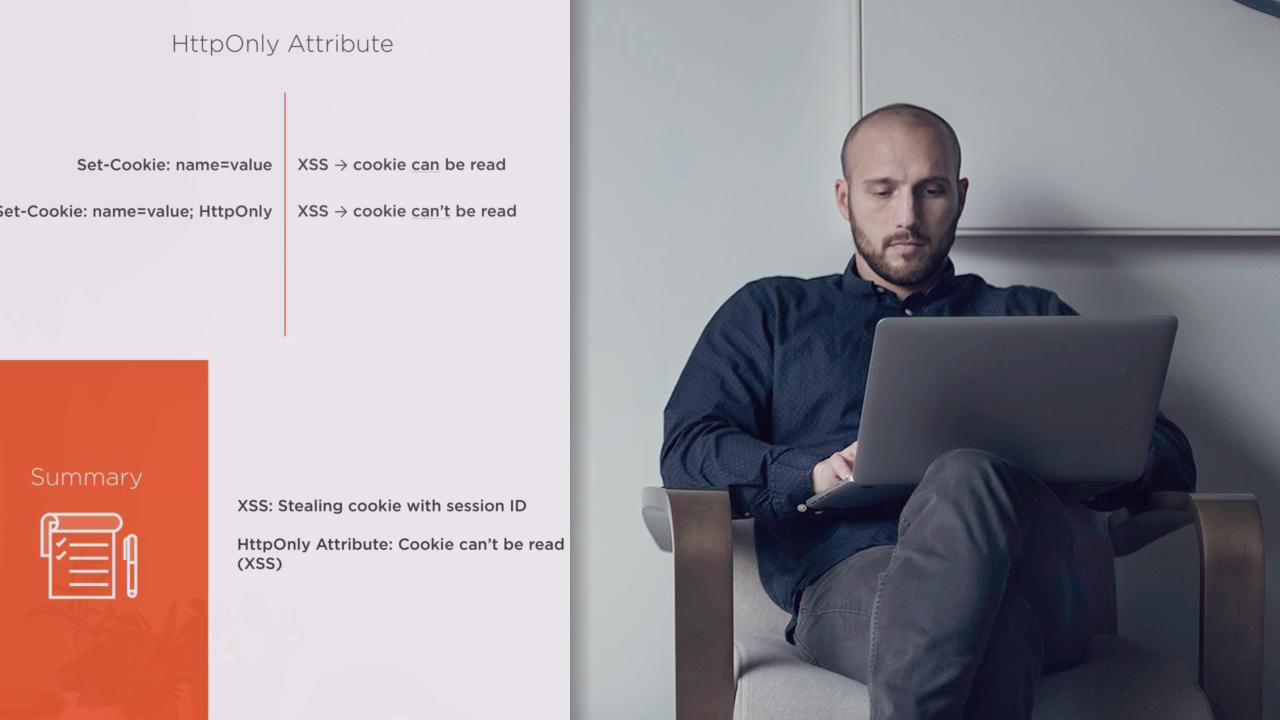
Cookies are interesting for attackers because of the sensitive data they store. This course, Web App Hacking: Cookie Attacks, will teach you how to avoid the severe consequences of insecure cookie processing. First, you'll learn how cookies with sensitive data can leak over insecure channel. Next, you'll learn how the attacker can hijack cookies remotely. You'll also learn about weaknesses in cookie lifecycle and see one of the most underestimated cookie attacks - XSS via cookie. Finally, you'll learn how the attacker can tamper remotely with cookies of the user. By the end of the course, you'll know how cookie attacks work in practice and how to test web applications for various cookie processing flaws. What's more, you will learn how to process cookies securely.

