- Course
Credential Access with Hashcat
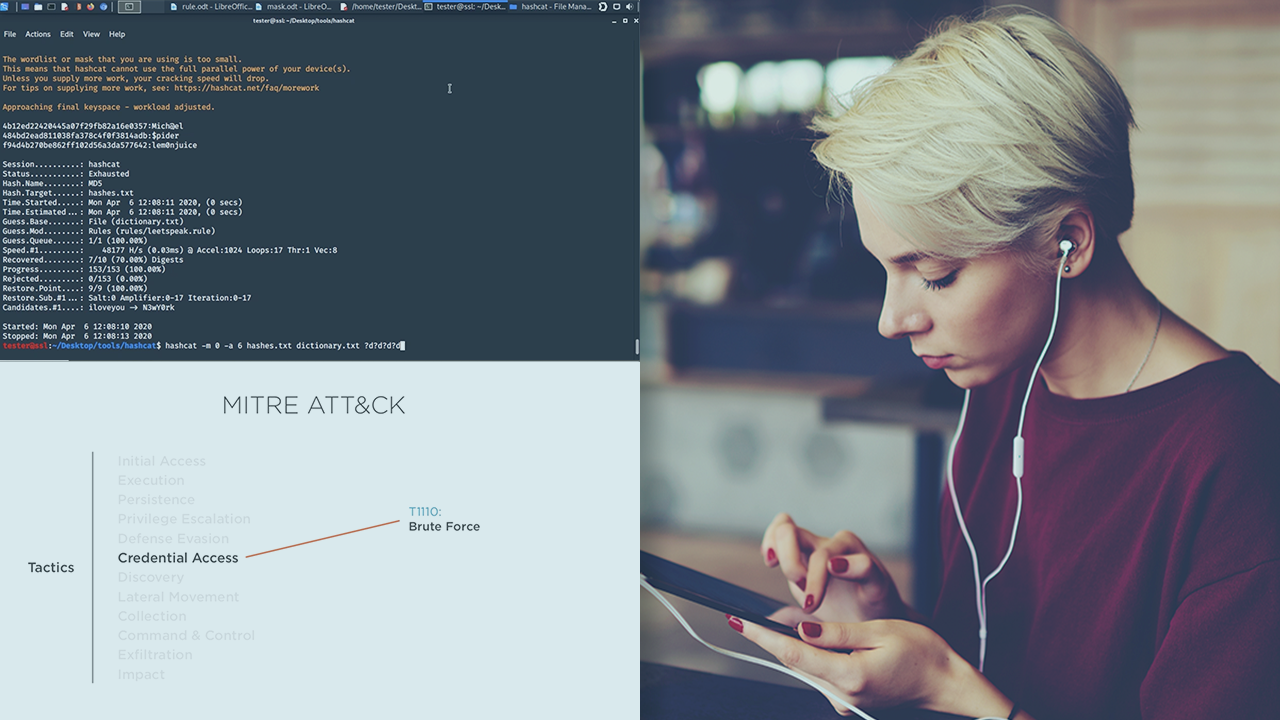
Hashcat is the number one offline password cracker used by red team members and penetration testers. If you want to learn how to use Hashcat to crack passwords with different password cracking techniques, then this course is for you.
- Course
Credential Access with Hashcat
Hashcat is the number one offline password cracker used by red team members and penetration testers. If you want to learn how to use Hashcat to crack passwords with different password cracking techniques, then this course is for you.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Red team members and penetration testers need to know how to crack passwords with different password cracking techniques. In this course, Credential Access with Hashcat, you will learn about Hashcat, the number one offline password cracker. First, you will see how to launch a dictionary attack using Hashcat. Next, you will discover how you can crack more passwords when you launch a dictionary attack with a rule. Then, you will learn how to launch a dictionary attack with a mask, also known as a hybrid attack). Finally, you will explore how to use Hashcat to crack password-protected PDF and DOCX files. By the end of this course, you will know how to use Hashcat to crack passwords with different password cracking techniques.

