- Course
Credential Access with John the Ripper
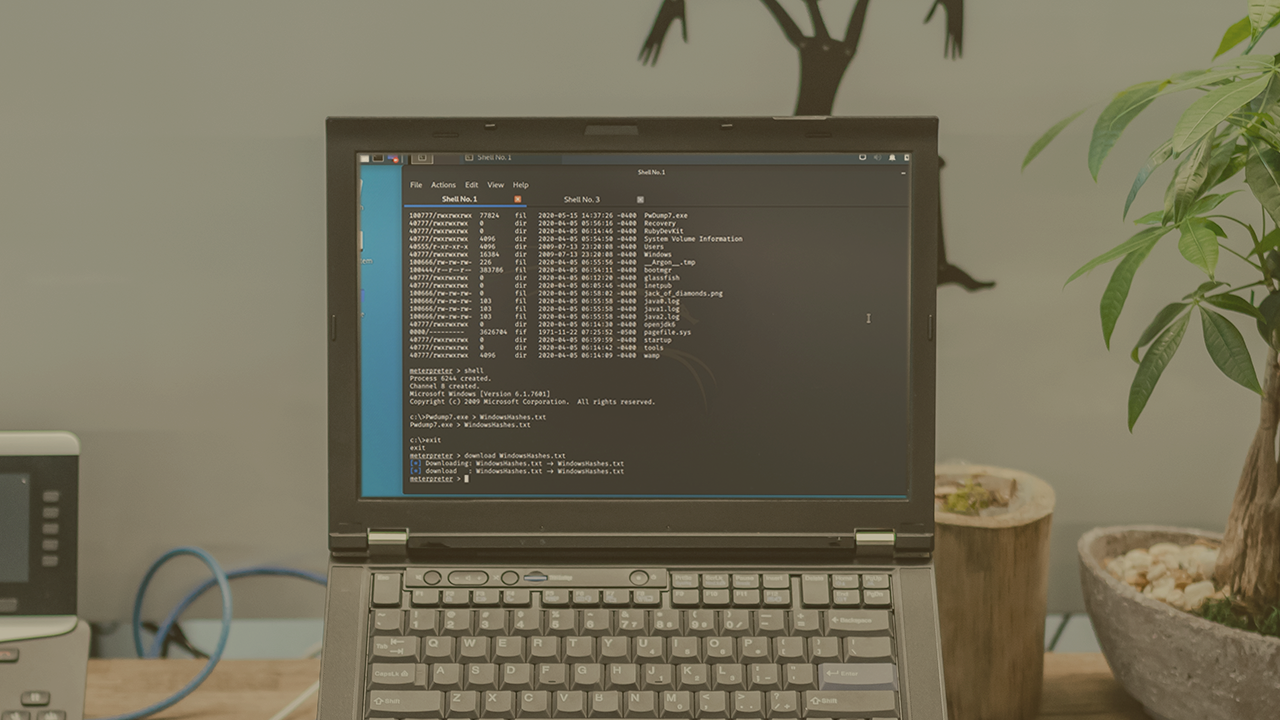
John the Ripper (JtR) is widely used within red team assessments. Learn how to leverage the powerful capabilities of JtR to crack passwords of various hash types and use JtR within Metasploit.
- Course
Credential Access with John the Ripper
John the Ripper (JtR) is widely used within red team assessments. Learn how to leverage the powerful capabilities of JtR to crack passwords of various hash types and use JtR within Metasploit.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Performing password cracking is a common task performed in a red team engagement. Understanding how to use the tools can be a daunting task. In this course, Credential Access with John the Ripper, you will gain the ability to crack commonly used password hashes leveraging the highly customizable tool, John the Ripper. First, you will learn how to navigate the syntax of John and amp up your cracking capabilities by obtaining rich wordlists and permutating them. Next, you will discover how to perform password cracking of common operating systems such as Windows and Linux. Finally, you will explore how to use John within a Metasploit session, giving you the ability to perform password cracking during the exploitation phase. When you are finished with this course, you will have the skills and knowledge of John the Ripper needed to amplify your red team engagements when performing password cracking.

