- Course
Getting Started with Wireshark
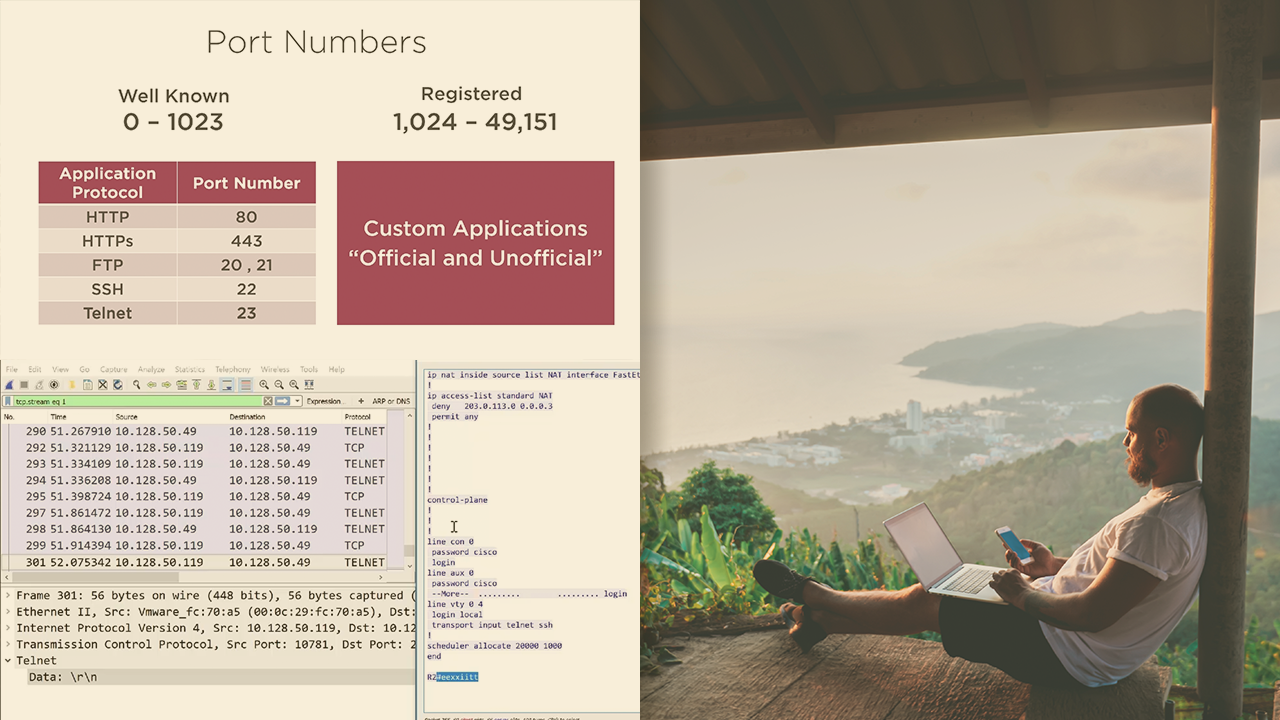
This course will introduce you to Wireshark operation, and provide the skills needed to capture traffic, filter out unneeded messages, and analyze the protocols in use.
- Course
Getting Started with Wireshark
This course will introduce you to Wireshark operation, and provide the skills needed to capture traffic, filter out unneeded messages, and analyze the protocols in use.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
In this course, Getting Started with Analyzing Network Traffic Using Wireshark, you will learn that Wireshark is a powerful and free utility used by network engineers, system administrators, and developers alike. First, you will get started with packet capture operation. Then, you will explore how to provide a primer on the Wireshark interface as well as how to interpret the data collected. Finally, you will discover how to use capture filters and display filters to isolate needed traffic, the basics of TCP operation, as well as examine the protocol used when downloading a simple HTTP website. This is an excellent course for someone who is knowledgeable about network operation but would like to dive deeper into protocol analysis.

