- Course
Implementing and Performing Risk Management with ISO/IEC 27005
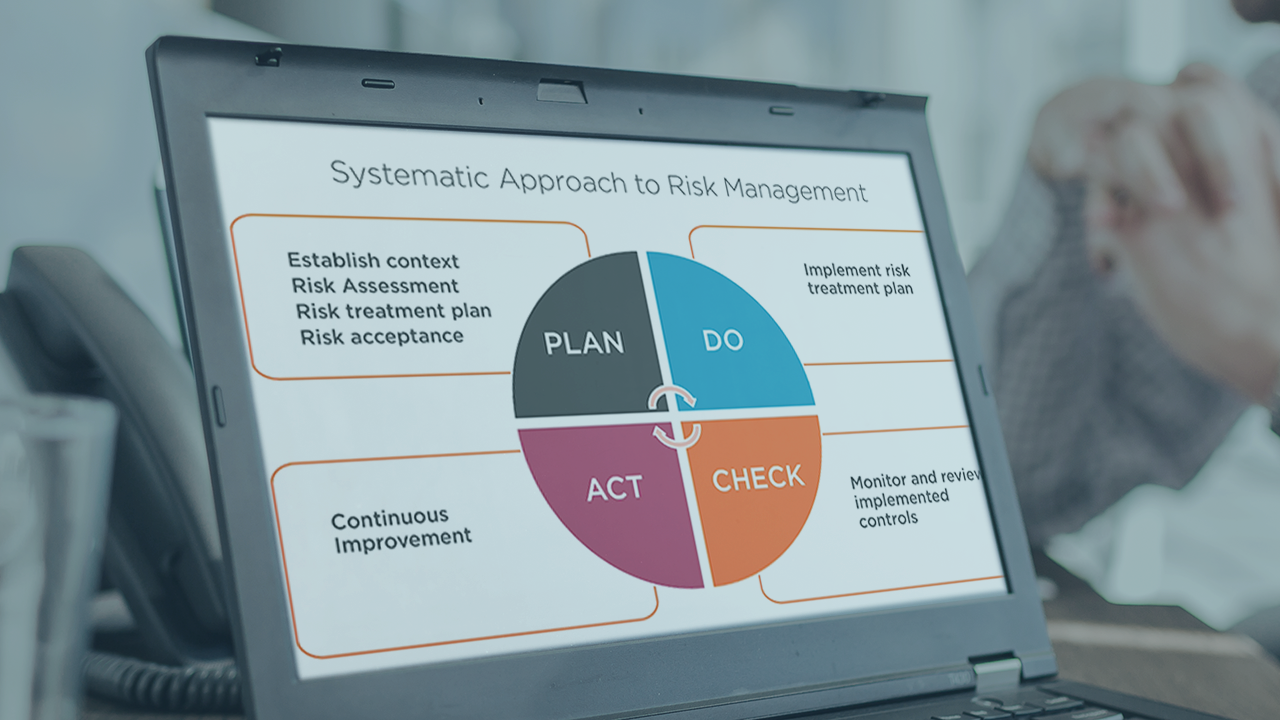
Everything you do in information security is related to risk, and no matter your discipline, sharpening your ISRM skills will increase your value. This course will arm you with a practical risk framework and approach to prioritize and address risk.
- Course
Implementing and Performing Risk Management with ISO/IEC 27005
Everything you do in information security is related to risk, and no matter your discipline, sharpening your ISRM skills will increase your value. This course will arm you with a practical risk framework and approach to prioritize and address risk.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Information security is a broad discipline, and security teams are increasingly strapped for time and resources. In this course, Implementing and Performing Risk Management with ISO/IEC 27005, you will find a practical framework to prioritize and orchestrate a comprehensive information security risk framework. First, you will learn about the internationally accepted risk management standard ISO/IEC 27005. Next, you will arm yourself with skills to establish the business risk context, assess business risks, and perform risk treatment. Finally, you will be equipped with meaningful approaches to effectively communicate and monitor your organization's risk. When you're finished with this course, you will have the knowledge and blueprint to coordinate a widely accepted framework and to bolster your organization's information security program.

