- Course
Initial Access with sqlmap
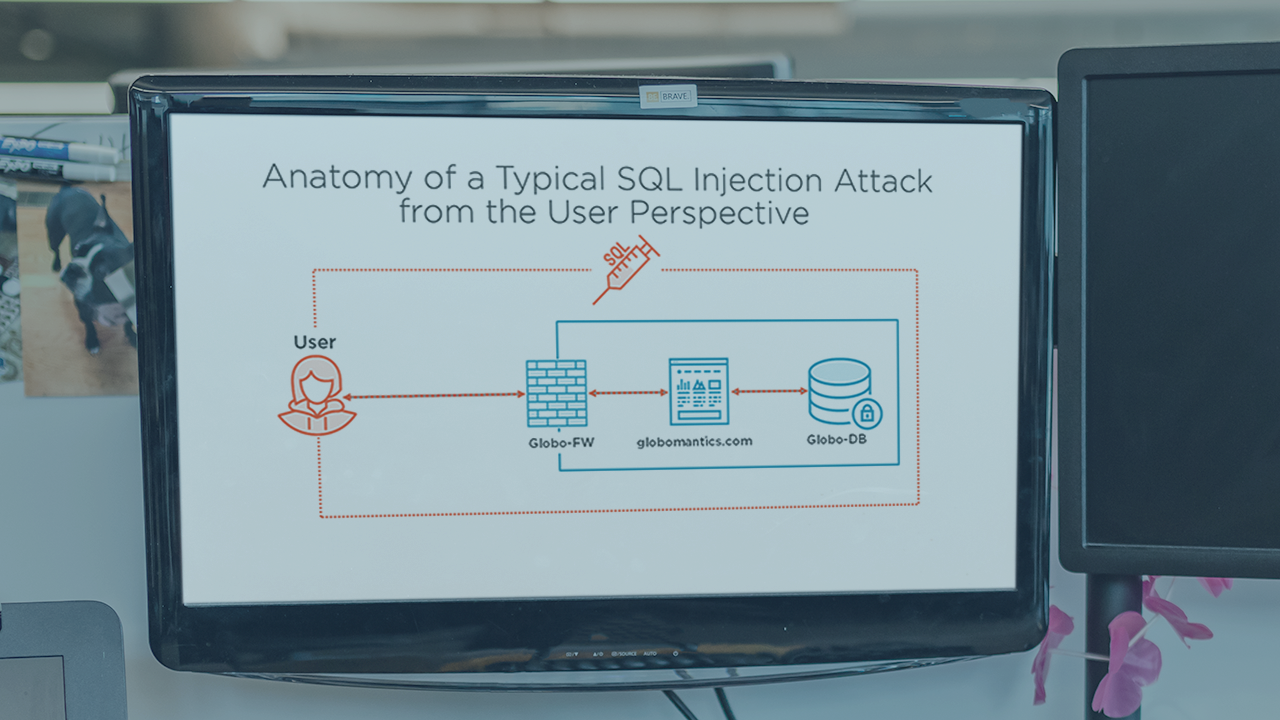
sqlmap is a powerful automation tool for identifying and exploiting SQL injection flaws. Add another tool to your toolbox by using sqlmap to exfiltrate data and gain initial access.
- Course
Initial Access with sqlmap
sqlmap is a powerful automation tool for identifying and exploiting SQL injection flaws. Add another tool to your toolbox by using sqlmap to exfiltrate data and gain initial access.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
SQL injection flaws are one of the most critical application vulnerabilities. They can affect any application that uses a database, and a single flaw can lead to data loss or even server compromise. In this course, Initial Access with sqlmap, you'll learn how to use this powerful tool to identify and exploit a variety of SQL injection flaws in a red team environment. First, you'll discover how to setup sqlmap's command line and test authenticated web pages. Next, you'll use sqlmap's built-in enumeration tools to exfiltrate user data. Then, you'll delve into tuning sqlmap's parameters when crawling applications. Finally, you'll exploit a SQL injection to gain initial system access. When you're finished with this course, you'll have the skills and knowledge of sqlmap needed to streamline the process of finding and exploiting SQL injection flaws.

