- Course
Microsoft 365 Mobility and Security: Security and Threat Management
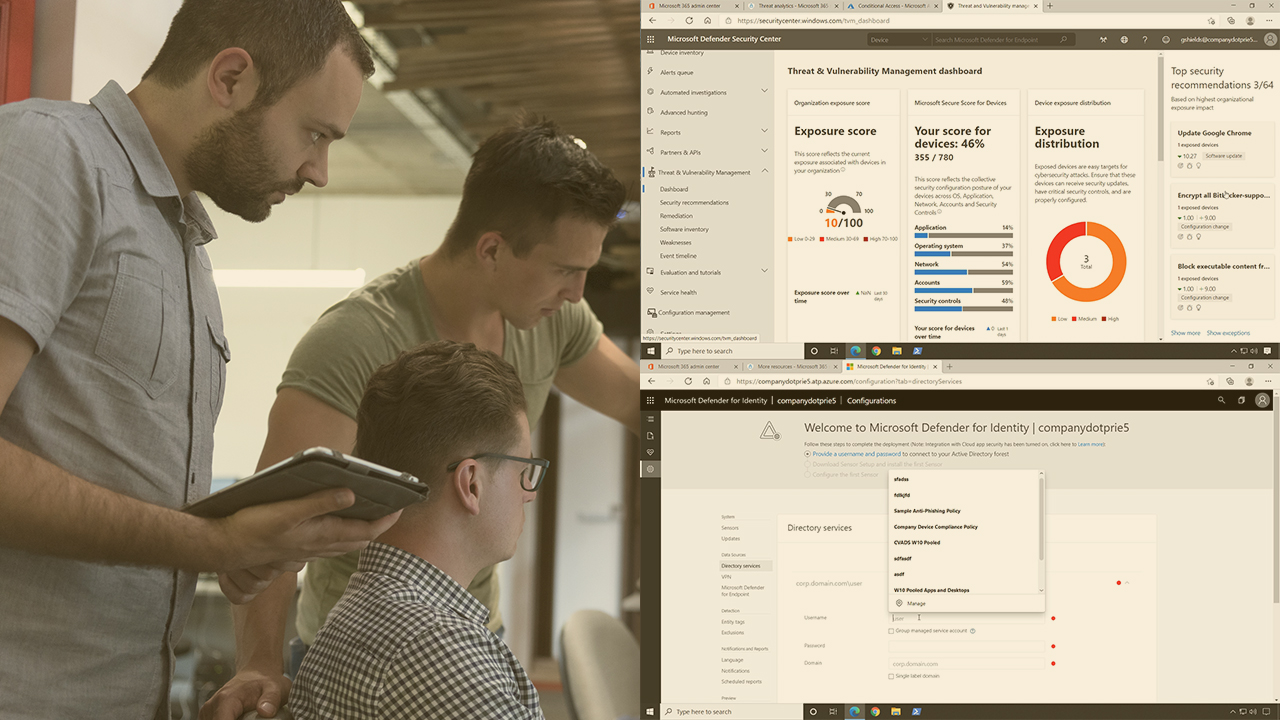
Explore the solutions and the integration of Microsoft Defender for Office 365, Microsoft Defender for Identity, Microsoft Cloud App Security, and Microsoft Defender for Endpoint in this course.
- Course
Microsoft 365 Mobility and Security: Security and Threat Management
Explore the solutions and the integration of Microsoft Defender for Office 365, Microsoft Defender for Identity, Microsoft Cloud App Security, and Microsoft Defender for Endpoint in this course.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
Microsoft 365 comes equipped with a broad array of security and threat management solutions. So many, in fact, that the most difficult part of using them is first understanding them, and knowing where one feature set ends and the others begin.
In this course, Microsoft 365 Mobility and Security: Security and Threat Management, the third course of four in this learning path, you'll start with a broad exploration of the threat protection solutions with Microsoft Defender. First, you'll implement Defender for Office 365 policies, integrate Defender for Identity, and then Defender for Endpoint to aggregate security signals across your cloud, server, and device components. Next, you'll plan and implement Microsoft Cloud App Security to discover and control the cloud applications used by our users. Finally, you'll explore, once integrated, the visualizations and dashboards these solutions surface that provide deep-level access to bad behaviors, malware activities, and inappropriate application accesses. By the end of this course, you'll have an understanding of the features and integrations between the threat management solutions spanning from Office 365 security policies, to Azure identity security, to Cloud App Security, and even down to the individual device with Defender for Endpoint.

