- Course
Network Vulnerability Scanning with OpenVAS
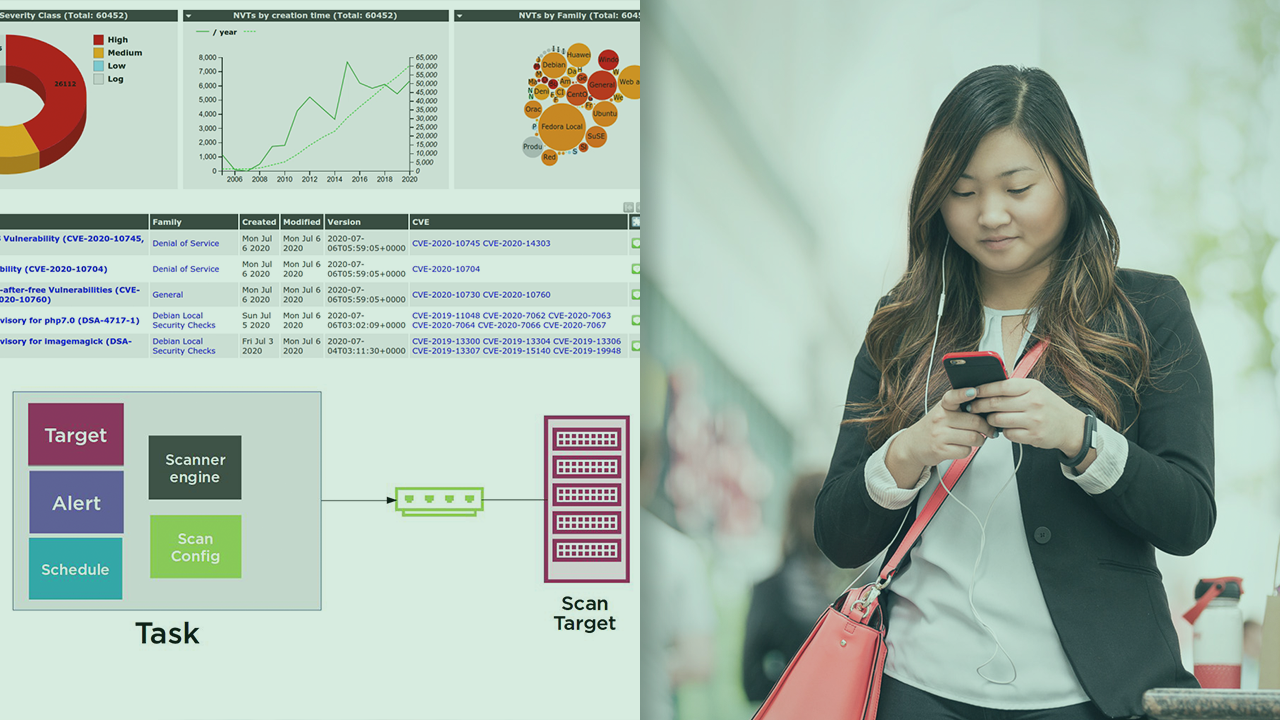
Before launching a penetration testing session, you must first assess the target network and its compute resources for known vulnerabilities. The OpenVAS suite is built to perform complete and effective vulnerability scans. Learn how it's done.
- Course
Network Vulnerability Scanning with OpenVAS
Before launching a penetration testing session, you must first assess the target network and its compute resources for known vulnerabilities. The OpenVAS suite is built to perform complete and effective vulnerability scans. Learn how it's done.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Greenbone Vulnerability Manager's OpenVAS vulnerability assessment suite brings together an actively curated database of vulnerabilities with powerful network scan and reporting tools. In this course, Network Vulnerability Scanning with OpenVAS, you’ll learn to test your infrastructure for dangerous vulnerabilities. First, you’ll install and configure OpenVAS on Kali Linux. Next, you’ll come to understand the roles played by each of the public vulnerability databases on which vulnerability scanning relies. Finally, you'll launch a range of scans against live targets, and make sense of the reports that your scans will generate. When you’re finished with this course, you’ll have the skills and knowledge of OpenVAS needed to better secure your servers and IT resources.

