- Course
Performing OSINT Gathering on Employee Targets
Open Source Intelligence (OSINT) gathering applies to not only companies but to employees as well. This course will teach you how to gather various forms of employee OSINT, including historical, social, mobile, and physical information.
- Course
Performing OSINT Gathering on Employee Targets
Open Source Intelligence (OSINT) gathering applies to not only companies but to employees as well. This course will teach you how to gather various forms of employee OSINT, including historical, social, mobile, and physical information.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
As organizations focus their efforts on protecting their technical infrastructure, far too many leave their most vulnerable assets exposed to attack: their people. In this course, Performing OSINT Gathering on Employee Targets, you will gain the ability to gather and analyze OSINT related to an organization’s workforce members. First, you will learn useful tools and techniques for collecting employee OSINT. Next, you will analyze your data, extracting information that might hold value to an attacker. Finally, you will explore how to incorporate your findings into preparing social engineering attacks. When you’re finished with this course, you will have the skills and knowledge of employee OSINT gathering needed to conduct an effective, worthwhile penetration test, and to help the target organization better understand how to protect their employees.
Performing OSINT Gathering on Employee Targets
-
Preparing to Perform Employee OSINT | 1m 23s
-
What Is OSINT? | 2m 25s
-
Why Is OSINT Important? | 3m 55s
-
OSINT Analysis | 2m 26s
-
How Effective Is OSINT Gathering? | 1m 2s
-
The Penetration Testing Execution Standard (PTES) | 2m 43s
-
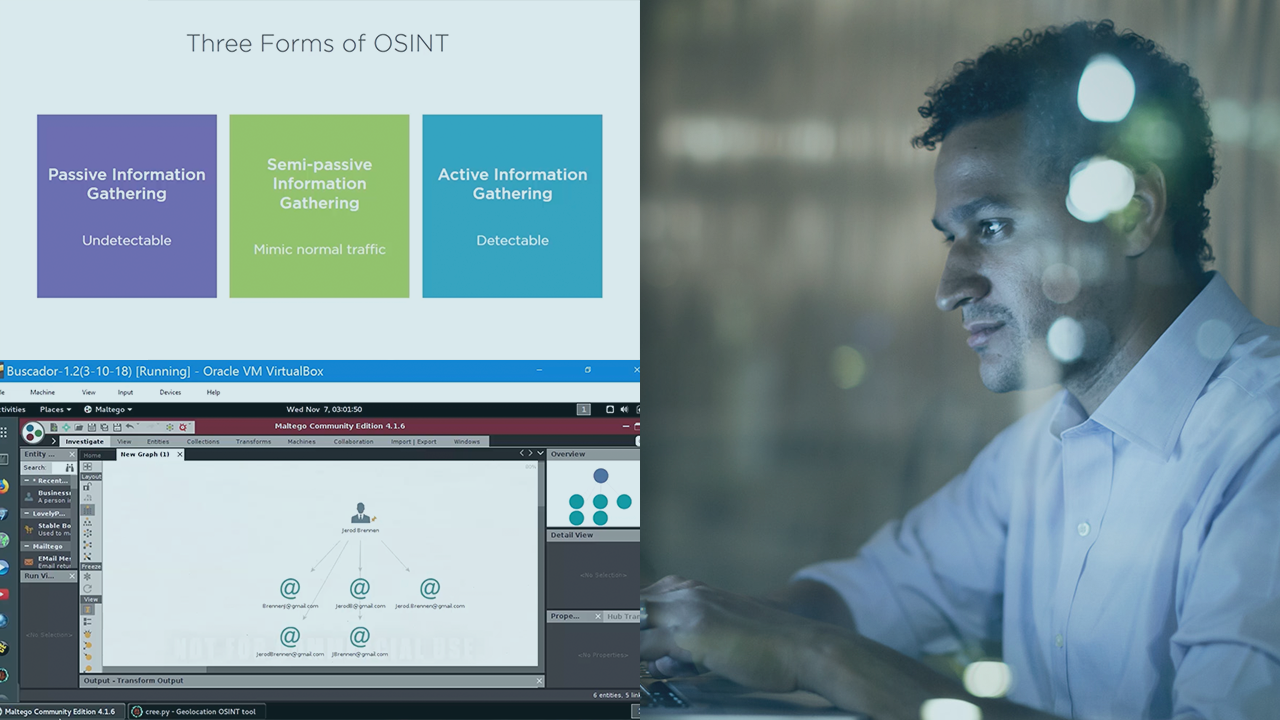
Three Forms of OSINT | 3m 32s
-
What Does OSINT Entail? | 3m 38s
-
Preparing Your Testing Environment | 3m 59s
-
Virtual Machine Players | 3m 52s
-
Summary | 35s

