- Course
OWASP Top 10: API Security Playbook
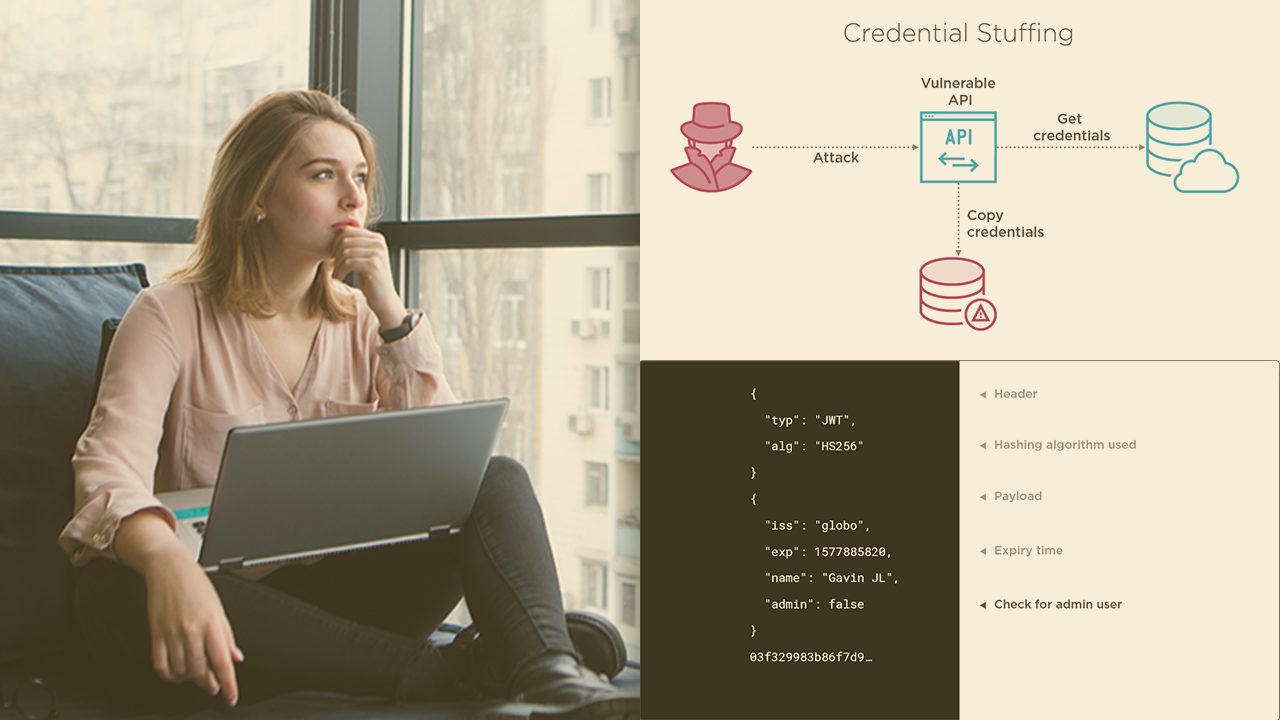
APIs are crucial to the internet and their security is vital to both their creators and consumers. This course will teach you about each of the OWASP API Top 10 vulnerabilities, helping you to identify and prevent them in your APIs.
- Course
OWASP Top 10: API Security Playbook
APIs are crucial to the internet and their security is vital to both their creators and consumers. This course will teach you about each of the OWASP API Top 10 vulnerabilities, helping you to identify and prevent them in your APIs.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Application Programming Interfaces (APIs) form the foundation of numerous web technologies, including Software as a Service (SaaS), mobile applications, web applications, and Internet of Things (IoT). API security is critical to keep those services and their customers secure. In this course, OWASP Top 10: API Security Playbook, you’ll learn strategies and solutions to mitigate the ten most important vulnerabilities for APIs. First, you’ll explore the attack, seeing how a vulnerability can be exploited. Next, you’ll discover the impact of the attack, how it can affect the API, the business and its customers. Finally, you’ll learn how to mitigate the vulnerability, using a selection of common defenses to reduce the risk of an effective attack. When you’re finished with this course, you’ll have the skills and knowledge to help protect you from the top ten API vulnerabilities, the most critical vulnerabilities to your API.

