- Course
Providing Secure Cloud Applications
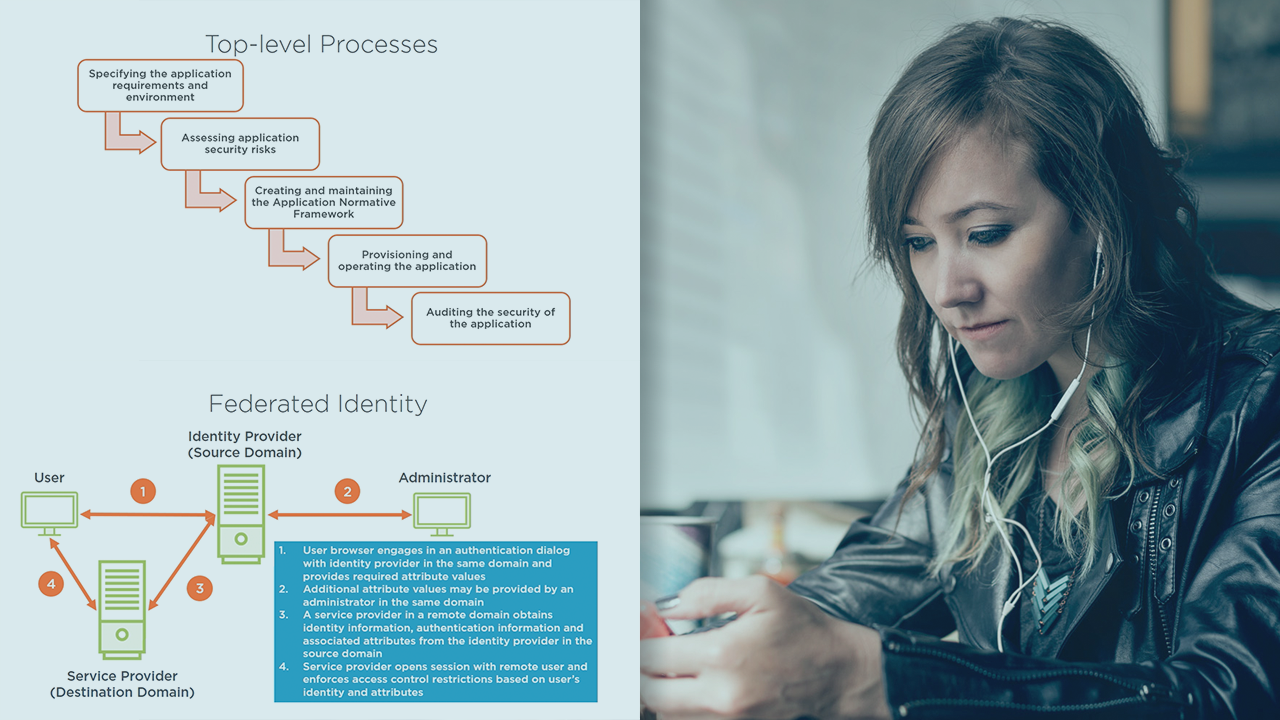
Cloud Computing is changing industries and careers. This course will train you to design secure cloud applications, how to successfully migrate legacy applications to the cloud, and how to securely operate in the cloud computing environment.
- Course
Providing Secure Cloud Applications
Cloud Computing is changing industries and careers. This course will train you to design secure cloud applications, how to successfully migrate legacy applications to the cloud, and how to securely operate in the cloud computing environment.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Cloud
- Security
What you'll learn
Cloud computing has rocked every industry and has completely redefined enterprise information technology. Developers must now use DevSecOps, Serverless Computing, and Microservices to invent and deploy entirely new business models. In this course, Providing Secure Cloud Applications, you will learn how to do this in a secure manner. First, you will learn how to design a secure cloud application. Next, you will discover how to successfully migrate legacy applications to the cloud. Finally, you will explore how to securely operate in the cloud computing environment. When you have finished this course, you will be prepared to develop and deploy secure cloud applications that deliver true value to your organization.

