- Course
Requirements, Planning, Direction, and Review (C|TIA Prep)
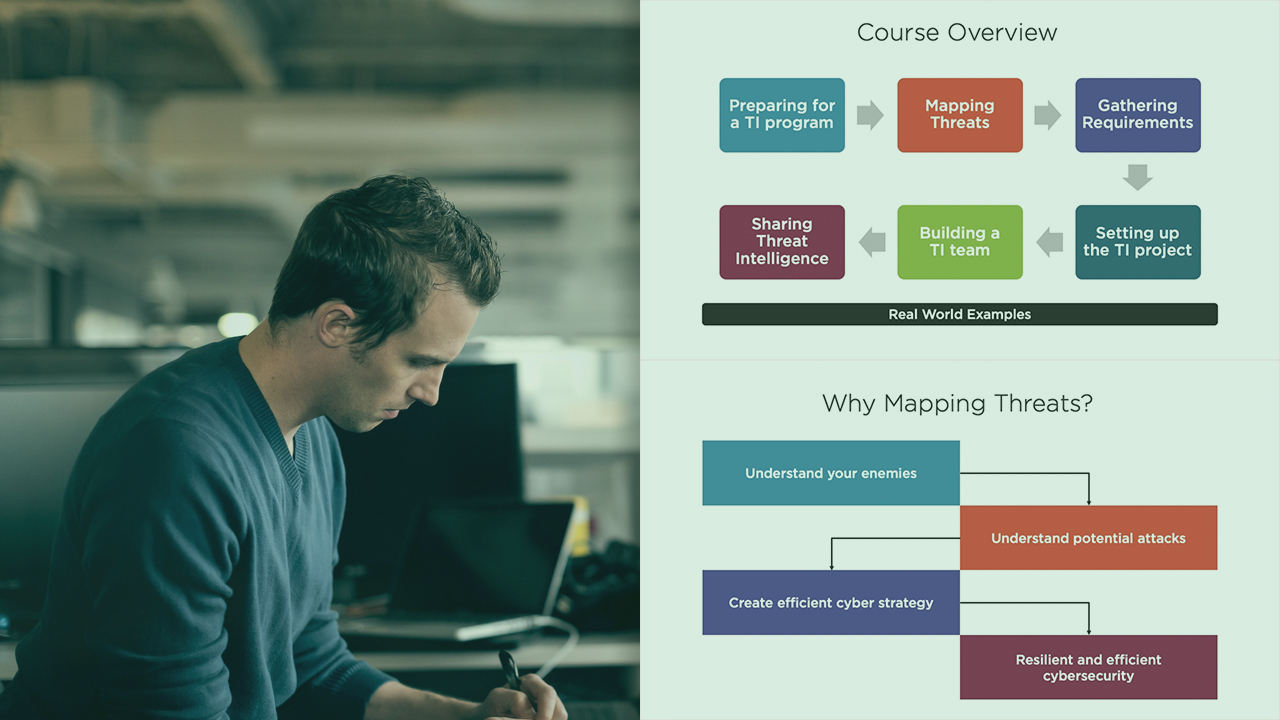
Planning and designing a threat intelligence program is one of the most important skills of threat intelligence specialist. This course will teach you how to gather requirements, plan, design, direct and review a threat intelligence program.
- Course
Requirements, Planning, Direction, and Review (C|TIA Prep)
Planning and designing a threat intelligence program is one of the most important skills of threat intelligence specialist. This course will teach you how to gather requirements, plan, design, direct and review a threat intelligence program.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Approaching cybersecurity with a threat intelligence mindset is an effective way of reducing the cyber risk of a company. By analyzing the specific threats to our business and ingesting the right threat intelligence data we can effectively tackle potential cyber-attacks. In this course, Requirements, Planning, Direction, and Review (C|TIA Prep), you will learn how to implement an effective Threat Intelligence program. First, you will explore how to prepare for a TI program, including how to map the potential threats to your business. Next, you will discover how to gather requirements for your program, which includes both business and technical needs. After that, you will cover how to translate the requirements into a program design. Finally, you will learn how to build a solid Threat Intelligence team and how to share the TI knowledge with the appropriated destinations (such as directors, SOC teams and external parties). When you’re finished with this course, you will have the skills and knowledge required to build an effective threat intelligence program in your company. This course covers the third chapter of the Cyber Threat Intelligence Analyst (C|TIA or CTIA) Certification.

