- Course
Cyber Security Awareness: Security Overview
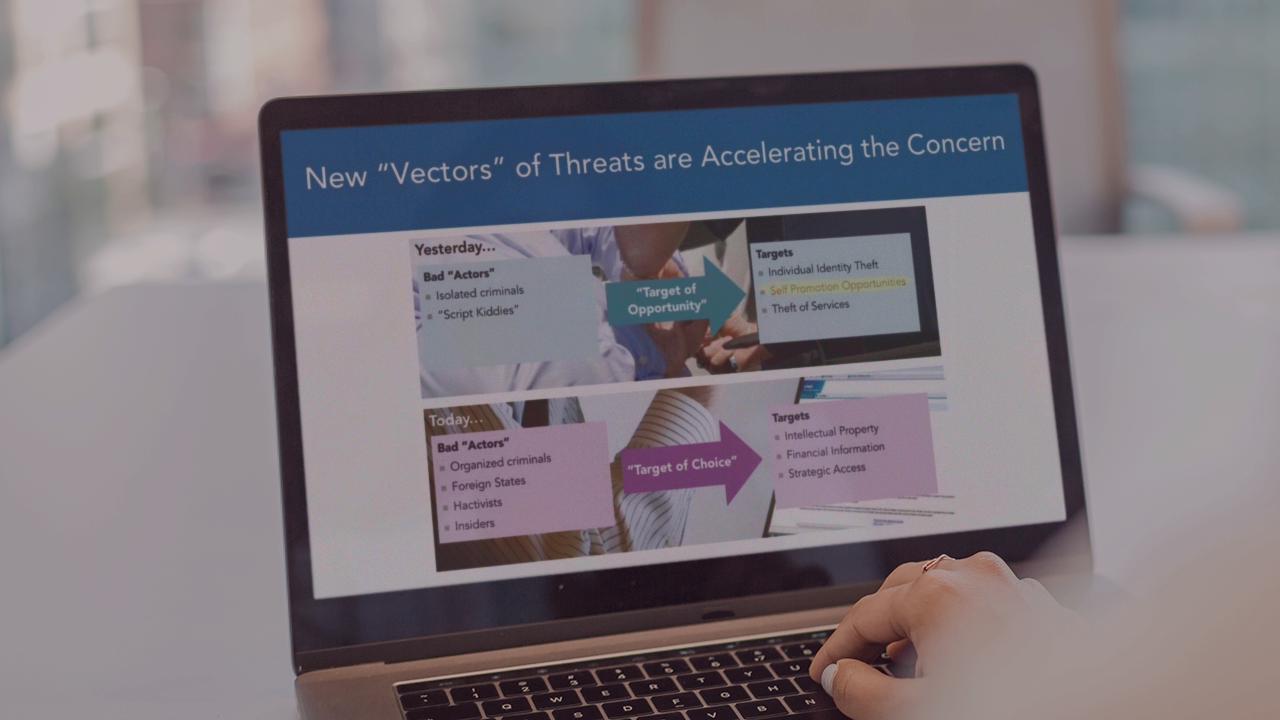
Overview to types of cyber security threats everyone should be aware of.
- Course
Cyber Security Awareness: Security Overview
Overview to types of cyber security threats everyone should be aware of.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
If you're someone who uses technology and has concerns about your digital security then this course, Cyber Security Awareness: Security Overview, is a great course for you. In this course, we will first cover different areas that are top priorities for security organizations. Then we will look at where threats are coming from in our current global environment before finally looking at the reality of cyber attacks in our current global environment.

