- Course
Testing Security Controls and Detecting Vulnerabilities with Nmap 7
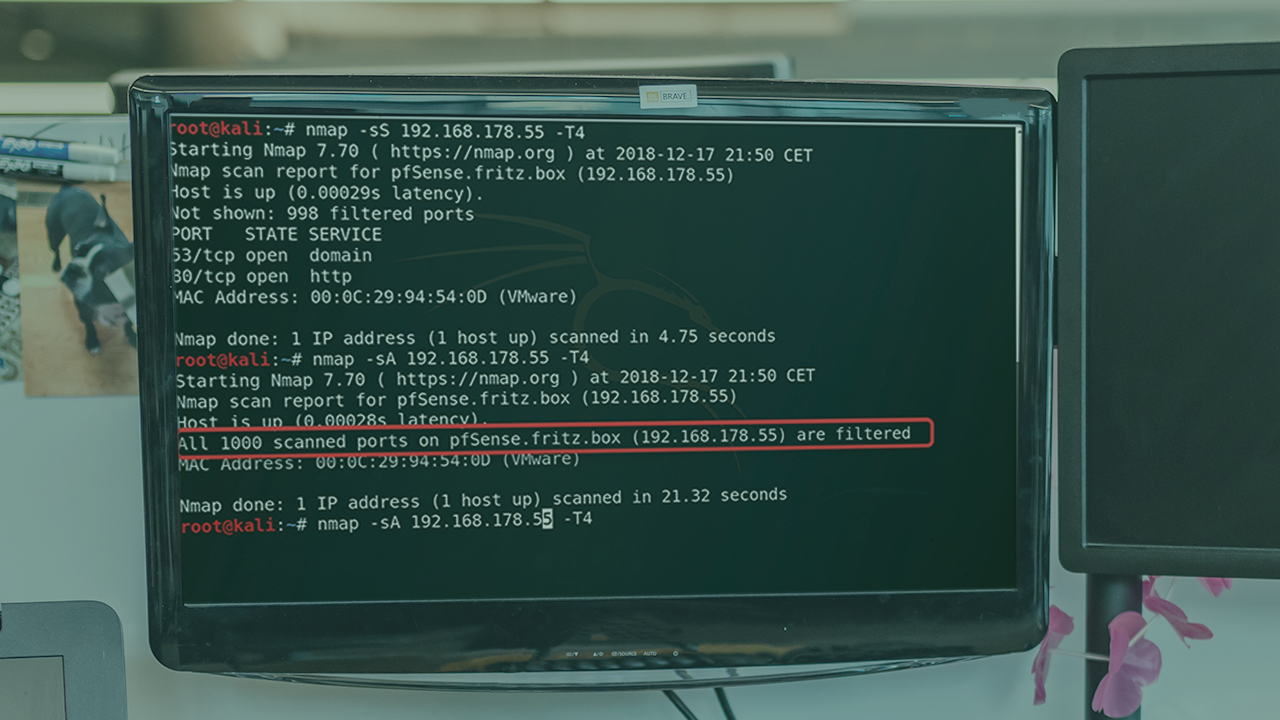
This course will help you will learn how to leverage the capabilities of Nmap to find insecure applications and explore the weaknesses in your organization’s firewalls.
- Course
Testing Security Controls and Detecting Vulnerabilities with Nmap 7
This course will help you will learn how to leverage the capabilities of Nmap to find insecure applications and explore the weaknesses in your organization’s firewalls.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Testing network security controls and discovering vulnerabilities are important parts of any organizations security plan. In this course, Testing Security Controls and Detecting Vulnerabilities with Nmap 7, you will learn how to do just that. First, you will learn how Nmap conducts host discovery. Next, you will see how to perform port scans. Finally, you will learn how Nmap detects applications and operating systems. After finishing this course, you will know how to leverage the capabilities of Nmap to find insecure applications and explore the weaknesses in your organization’s network security devices.

