- Course
Threat Modeling Methodologies
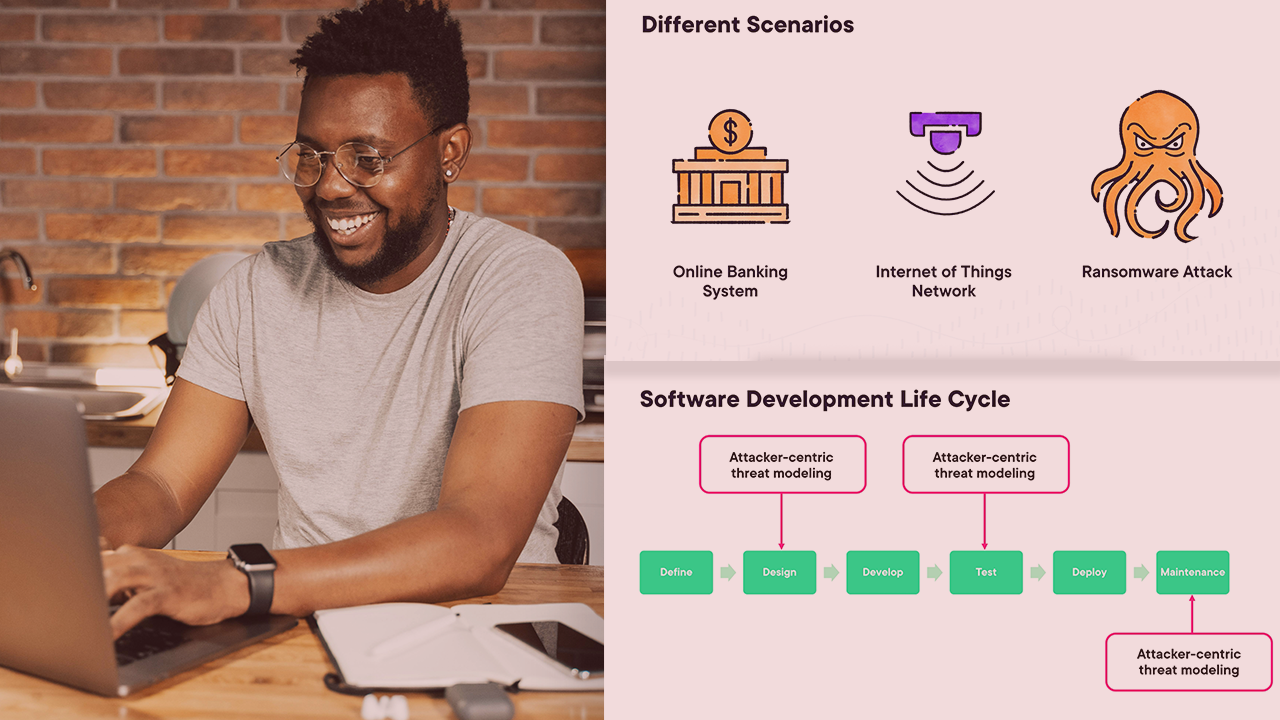
Threat modeling can inject more security into your software development lifecycle. This course will teach you all about the various threat modeling methodologies, their key elements, and how to choose the correct one for your specific application.
- Course
Threat Modeling Methodologies
Threat modeling can inject more security into your software development lifecycle. This course will teach you all about the various threat modeling methodologies, their key elements, and how to choose the correct one for your specific application.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Threat modeling is a growing field of interest for software architects, developers, and security professionals. In this course, Threat Modeling Methodologies, you’ll learn how to select the correct methodology. First, you’ll explore the various threat modeling approaches. Next, you’ll discover the different methodologies. Finally, you’ll learn how to pick the correct methodology for specific scenarios. When you’re finished with this course, you’ll have the skills and knowledge of thread modeling methodologies needed to apply the correct methodology in practice.

